Hello, folks!
We spend whole month for this feature and I would like to offer it here!
Since now we could do Deep Packet Inspection for attack fingerprints! 🙂 Very big thanks to nDPI folks which could do nice platform for this task!
So, instead of very less informative logs like:
2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1
We could generate really useful logs like this:
Protocol: DNS query_type: 1 query_class: 1 rsp_code: 0 num answers: 0, num queries: 1 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 Protocol: HTTP 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 Protocol: HTTP 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 Protocol: HTTP 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 Protocol: HTTP 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 Protocol: HTTP 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 Protocol: HTTP 2015-07-29 22:31:34.081626 188.40.35.183:80 > 37.190.50.41:18037 protocol: tcp flags: syn,ack frag: 0 packets: 1 size: 74 bytes ttl: 0 sample ratio: 1 For enabling this feature you should do following records in /etc/fastnetmon.conf: collect_attack_pcap_dumps = on process_pcap_attack_dumps_with_dpi = on
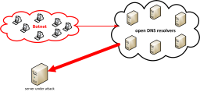
Finally! We have finished some tests and could offer full support for most popular attack types:
NTP amplification
DNS amplification
SSDP amplification
SNMP amplification
And many else!
If you have some specific or new attack types which not detected by nDPI, please feel free to share it with us and we will contribute they to nDPI like this.
Cheers!