Increasingly, business is done online. This increases the risk of exposure to costly service interruptions caused by cyberattacks. Distributed Denial of Service (DDoS) attacks have emerged as one of the most common and impactful attack vectors aimed at business networks.
Today, DDoS attacks account for 40% of all cybersecurity incidents, with some organisations facing multiple attacks per day. With the average throughput of volumetric attacks rising by over 3X in the last decade, DDoS prevention has become essential for any organisation that relies on its network infrastructure to do business.
Business Consequences of DDoS Attacks
DDoS attacks can have a range of business consequences, most commonly including:
Downtime of key systems and applications
Disruption of internal and partner operations
Consumption of IT time and resources
Emergency recovery costs
Attacks disrupt your organisation’s network. Every second that passes without restoring normal operations can lead to mounting costs, user dissatisfaction, and missed opportunities. Stable and reliable network uptimes are critical for meeting SLAs and KPIs.
Near-Instant DDoS Detection
FastNetMon’s fast, reliable, and automated solution offers unparalleled relief for our business partners by keeping their networks up and running. Our solution is among the fastest detection technologies on the market. How fast? It can detect sFlow and SPAN/Mirror modes in under two seconds and Netflow 5/9 and IPFIX in around 30 seconds.
FastNetMon’s network protection capabilities are the foundation of a DDoS mitigation program, providing the “brains” that power detection, mitigation, monitoring, and real-time visibility. Infinitely scalable and lightning-fast, FastNetMon is the ideal way to protect against large volumetric attacks.
Protect Your Network Infrastructure Try FastNetMon FREE for 1 Month |
What is DDoS Detection?
Detection is the first phase of protecting against network and protocol attacks. Organisations need technology that can quickly and accurately detect malicious traffic and apply the appropriate mitigation strategies.
FastNetMon is a versatile DDoS Detection tool, sensitive to a range of DDoS attack types:
- Flood attacks via UDP, TCP, ICMP
- IP Protocol attacks via fragmented packets
- TCP Protocol attacks via SYN, SYN-ACK, and FIN floods
- Amplification attacks via NTP, SNMP, SSDP, DNS, GRE, charges, and more
- Multi-vector attacks using a combination of techniques
FastNetMon can operate at scale without slowing down thanks to a high-performance real-time traffic processing engine implemented in C++. It supports various traffic telemetry protocols, including NetFlow, IPFIX, sFlow, and SPAN/port mirror (e.g., Amazon and Google VPC Flow Logs).
Have questions about DDoS Protection?
Check out our DDoS Protection FAQ. We answer common questions such as:
- Can our firewall/ISP/CDN protect us against DDoS attacks?
- Are cloud-based DDoS protection solutions more effective?
- What is the difference between DoS and DDoS?
How Does FastNetMon Detect Malicious Traffic?
FastNetMon supports a broad range of capture engines, including port mirroring, NetFlow, sFLOW, and IPFIX, which feed it information about incoming traffic. It can detect incoming attacks quickly based on increases in bandwidth usage, packet per second (Pps) count, and flow count. It also enables network engineers to alter each parameter based on past attack profiles.
FastNetMon gives network administrators full control over the detection and mitigation process, allowing them to design, configure, monitor, and manage DDoS defences that suit their organisation’s needs, budget, and network hardware.
With 2-second detection, FastNetMon responds to attacks the instant it receives traffic information from your network equipment (routers, switches, firewalls).
Why Use FastNetMon for DDoS Prevention?
Near-Instant Attack Detection | Unlimited Scalability | Highly Qualified Support | Quick and Easy Integration |
Lightning-fast detection times of 2 seconds for sFlow 5 and port mirror mode and 5-30 seconds for Netflow/IPFIX. | Lab-tested scalability up to 5TB and 3 million flows/single server. Plus, linear scaling to any number of clustered servers. | Qualified and experienced support staff are ready to assist with anything from a query to a full-blown DDoS incident. | FastNetMon requires no special hardware. Initial installation and configuration take just 40 minutes. |
Developer-Friendly | Vendor Support | Save Money | Network Engineer Friendly |
Integrate with your ecosystem and configure your unique attack profile via REST JSON API, callback scripts, and webhooks. Supports Graphite, Clickhouse, and InfluxDB, with optional Kafka support. | FastNetMon features wide-ranging network vendor support, including Cisco, Juniper, Dell, HP, D-Link, Fortinet, Nokia, Mellanox, Huawei, ZTE, Mikrotik, Ubiquiti, and more. | FastNetMon can reuse capabilities offered by your ISP to block attacks. It offers reliable integration with cloud scrubbing centres and reduces bills significantly via on-demand activation. | Easy configuration via the friendly command-line configuration tool fcli. |
Protect Your Growing Attack Surface from DDoS Attacks
Any device or software asset accessible via the Internet is part of your attack surface. The more Internet-connected software and hardware assets you have, the larger your attack surface. Digital transformation initiatives, in particular, result in a huge expansion of an organisation’s attack surface and spiralling cyber risk.
As your attack surface grows, it becomes more likely that you’ll be targeted with DDoS attacks—and their potential impact also grows. Being able to mitigate DDoS attacks is crucial, and your DDoS protection program should evolve as your network infrastructure grows.
FastNetMon is highly scalable and supports a range of DDoS mitigation services and strategies.
Mitigate DDoS Attacks with FastNetMon
FastNetMon is a complete network security solution that offers a full range of capabilities to monitor and protect your network. Beyond detecting attacks, FastNetMon features advanced DDoS mitigation capabilities to limit damage and disruption to your organisation and help you restore normal operations promptly.
Anti-DDoS Mitigation Strategies
We believe every organisation should be free to develop an anti-DDoS strategy that supports its needs, budget, and risk tolerance. To make this possible, FastNetMon enables organisations to automate DDoS mitigation strategies, including:
BGP BlackHole Automation
FastNetMon is compatible with all BGP implementations and bundled with BGP Unicast and BGP flow spec (RFC 5575). If an attack is detected, BGP will automatically be triggered to block or divert traffic from an attacked host. FastNetMon rapidly blocks sophisticated attacks, ensuring your network’s safety and uptime.

Flowspec DDoS Mitigation
Keep your legitimate traffic flowing while blocking malicious traffic using BGP FlowSpec-capable routers. Maintain business operations, manage customer experiences, and minimise downtime-related capital expenses while protecting your network and filtering malicious traffic.
Blocklist Filtering
Blocklist filtering is a routing-level anti-DDoS technique that blocks traffic originating from specified senders. This approach is highly effective for mitigating DDoS activity from sources known to be malicious and can also disrupt other threats, such as malware, e.g., by blocking communications with external C2 infrastructure. FastNetMon ingests data from threat feeds and updates the master blocklist with new and defunct threats in real time.

DDoS Scrubbing Center Diversion Automation
Diverting malicious network traffic to a scrubbing centre is one of the most effective ways to mitigate a DDoS attack. Malicious traffic is routed away from your network, allowing you to filter traffic while reducing your network load. FastNetMonsupports all scrubbing centres and can automatically reroute traffic when it detects an attack.
Traffic Visibility
FastNetMon maintains in-depth traffic data within an efficient storage system. This data is retained for years and allows you to instantly request customisable reports to get an in-depth understanding of your network’s traffic during any period.

Why Every Business Needs DDoS Protection
Maintain SLA-backed guarantees | Maintain Customer Satisfaction | Predictable Business Operations |
Breaching SLAs can lead to a loss of customer trust and increase the risk of financial losses and litigation. For service providers like ISPs, data centres, and cloud providers, DDoS protection can help protect your business by maintaining high service levels. | Successful attacks directly impact your bottom line—and they also cause indirect damage via frustrated and unserved users. Unresponsive, unavailable, or slow consumer-facing portals may be the result of a DDoS attack. | For mobile operators, ISPs, and VoIP operators, the network IS the business. Interruptions or unpredictable traffic patterns may disrupt your ability to conduct business. In this case, DDoS attacks directly threaten your bottom line. |
Improve Key Incident Response Metrics | Prevent Data Breaches | Digital Forensics |
Many businesses underperform on metrics like Mean Time To Detect and Respond (MTTD/MTTR). These metrics directly correlate with damage suffered due to an attack, especially when it comes to DDoS. | DDoS attacks are often a cover for more targeted attacks. Cybercriminals exploit this opportunity to access your data, exfiltrating or ransoming mission-critical or consumer information. | Determining a cyberattack’s exact course and timeline can help identify weak points in your network infrastructure. Network visibility and reporting capabilities support hardening against future incidents, as well as damage mitigation and remediation. |
FastNetMon Pricing
No matter the scale or complexity of their network, every business should have DDoS protection measures in place. FastNetMon’s catalogue of pricing packages scales with your requirements and budget, supporting the ideal implementation for your needs. We don’t limit the number of covered network devices, giving you peace of mind that your entire network is protected.
Our pricing starts at $115 USD per month. Not sure if it’s for you? Try FastNetMon FREE for 30 days and make up your own mind.
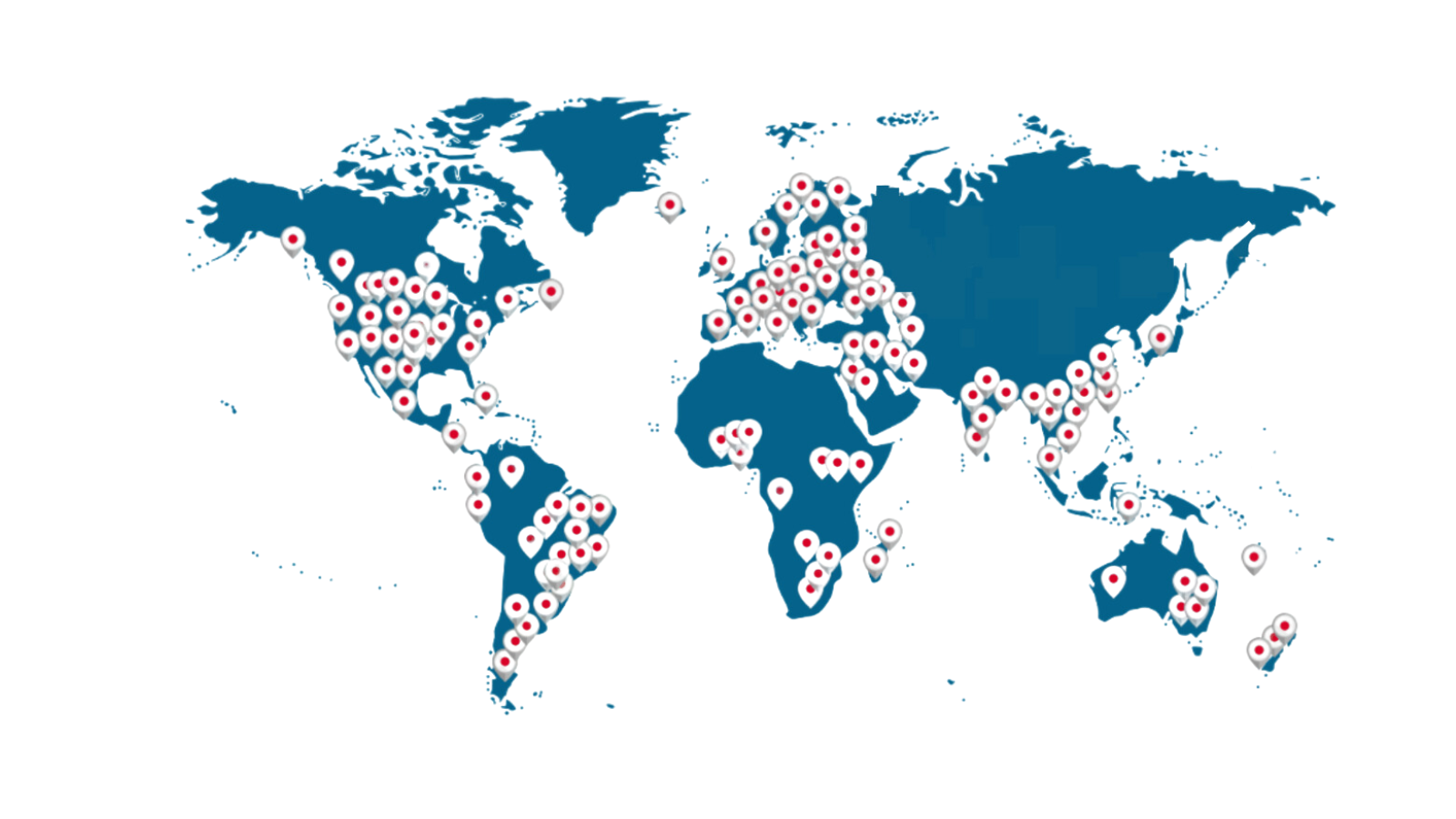
Our Customers
Customers in 134 countries trust FastNetMon as their DDoS mitigation provider.
94% of Trustpilot reviewers give us 5/5 stars!