Introduction to BGP Flow Spec
The frequency and scale of DDoS attacks are continuing to rise. Incidents involving hundreds of gigabits are becoming increasingly routine, and organisations face severe threats to their network infrastructures. BGP Flow Spec has become an essential tool for combating large volumetric attacks. Using BGP to propagate detailed traffic filtering rules throughout networks rapidly, BGP Flow Spec facilitates the real-time detection and blocking of malicious traffic based on specific criteria such as source/destination IP, port numbers, protocol type, and packet length. BGP Flow Spec serves as an initial line of defense against volumetric DDoS attacks, and, when combined with accurate and fast detection systems, it greatly improves the coordination to effectively mitigate these threats.
In this article, we lay out everything you need to know about BGP Flow Spec, and illustrate step-by-step how it works for DDoS mitigation.
What is BGP Flow Spec?
BGP Flow Spec is an extension to BGP (Border Gateway Protocol) that allows for the propagation of traffic flow specification rules. BGP Flow Spec introduces a set of enhancements to the standard BGP features to support the rapid distribution of traffic filtering and rate-limiting rules across the network. This capability is especially useful for preemptive traffic management, and therefore mitigating DDoS attacks. In other words, Flow Spec enables you to proactively deploy mitigation rules in real time when a DDoS attack is observed.
Brief History from RTBH to BGP Flow Spec
Historically, network administrators relied on techniques like Remote Triggered Black Hole (RTBH) filtering to mitigate DDoS attacks. RTBH works by directing traffic destined for an attacked host to a null route, effectively dropping the traffic before it can consume network resources. However, RTBH is somewhat blunt as it blocks all traffic to the targeted host, not just the malicious traffic.
As a more refined alternative, BGP Flow Spec was developed to allow for detailed specification of traffic flows to be blocked or redirected, without impacting legitimate traffic. This specificity is achieved through the use of multiple network layer and transport layer attributes to define flow specifications.
DDoS Mitigation Using BGP Flow Spec - full illustration
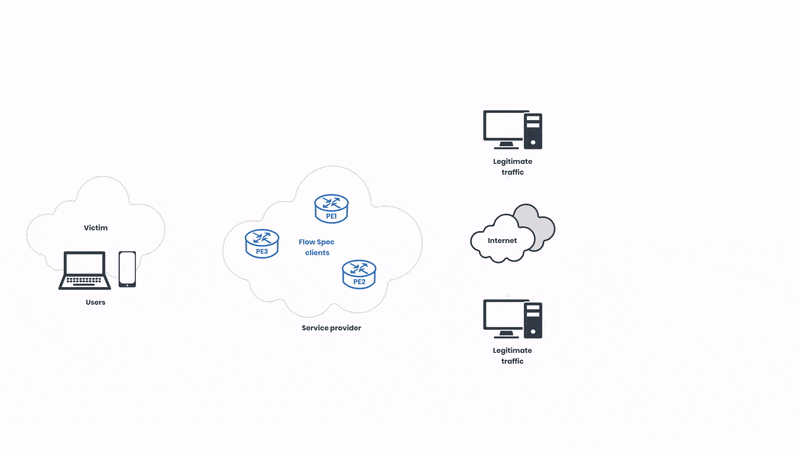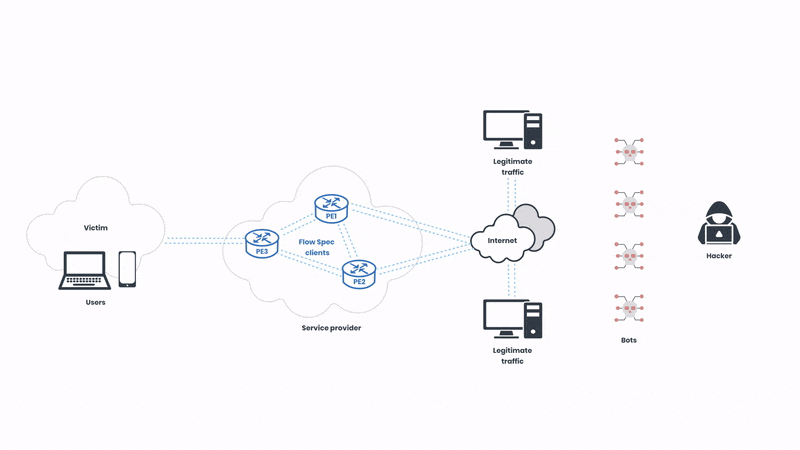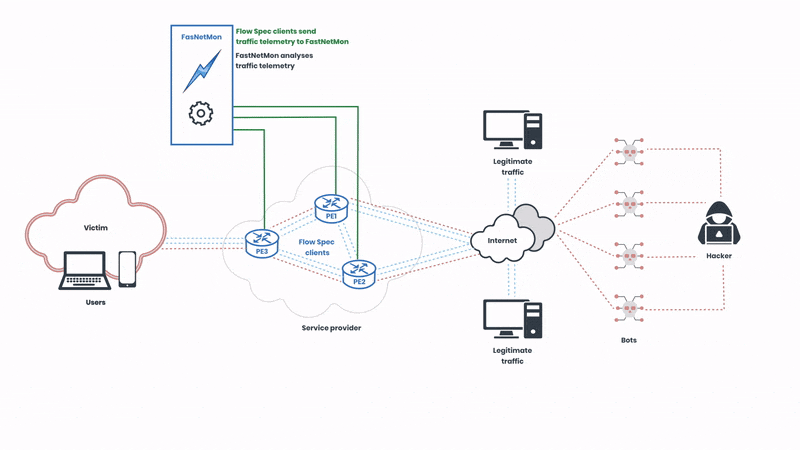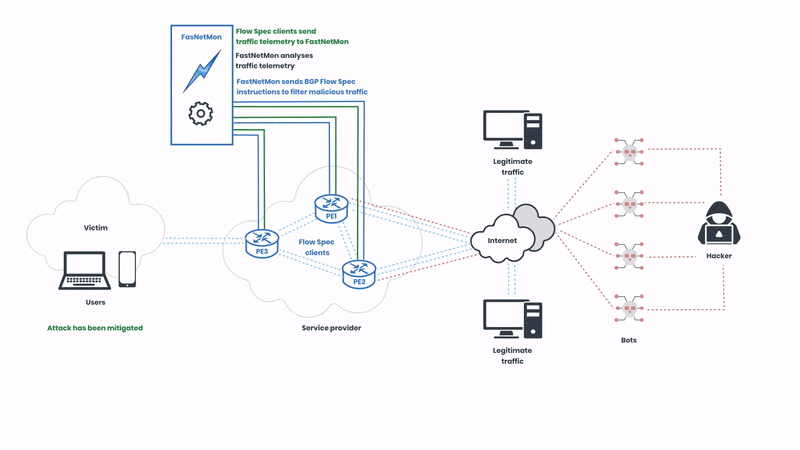
BGP Flow Spec works for DDoS mitigation by enabling precise control over traffic flows. We will walk you through how this works in practice and illustrate the traffic flows from the beginning of a DDoS attack to the post-mitigated state. First, let’s start with the complete picture, and then we will break it down step by step:
Now, let’s start from the beginning. First, we can see how the networks operate in a normal state before the attack:
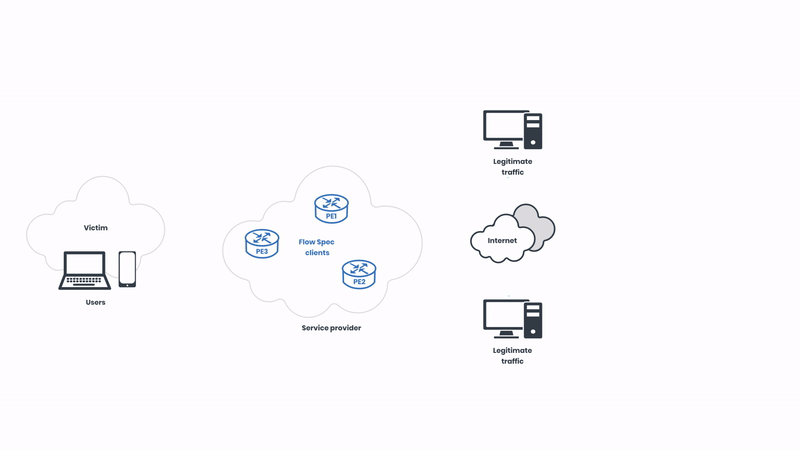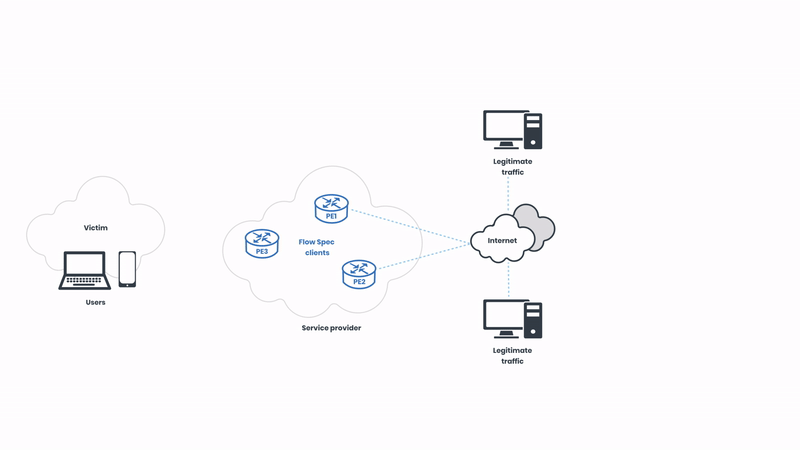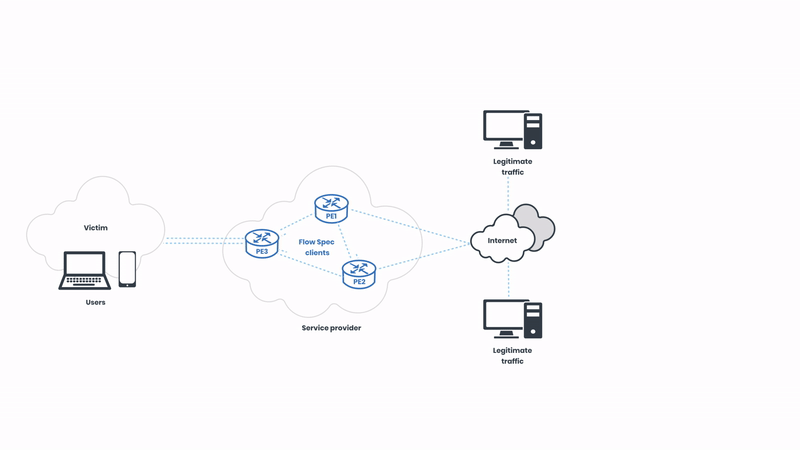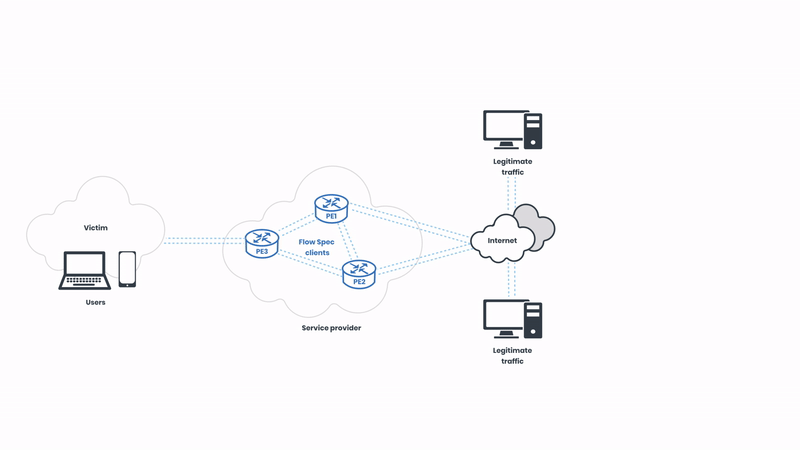
We have legitimate network traffic coming from multiple sources. In this case, the victim of the attack is pictured on the left side of the illustration. As usual, the attackers are targeting the “eyeballs”, intending to cause service disruption to the users. Let’s observe the attack unfolding:
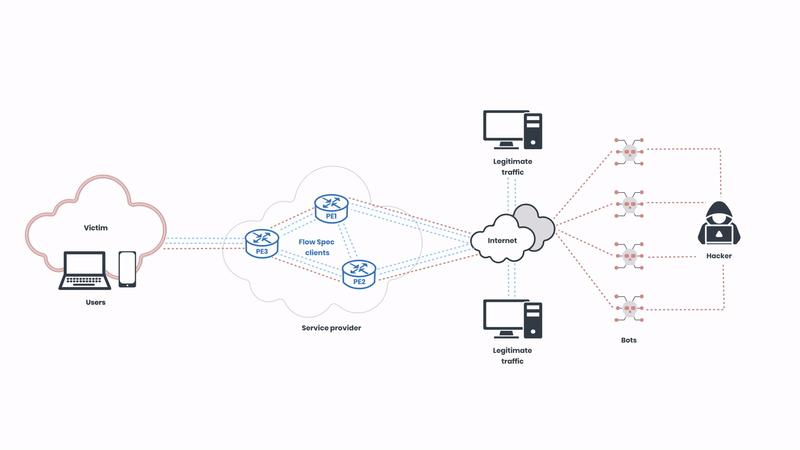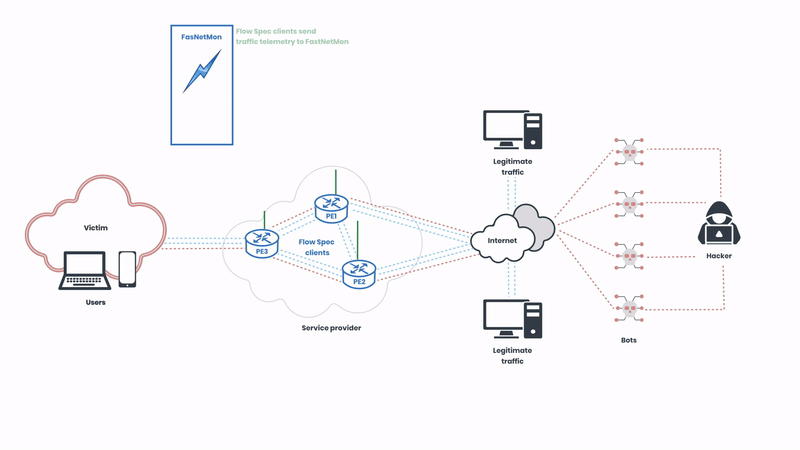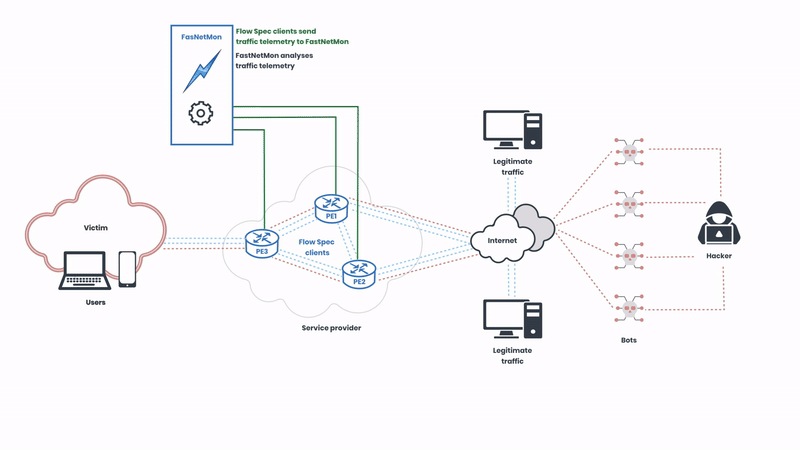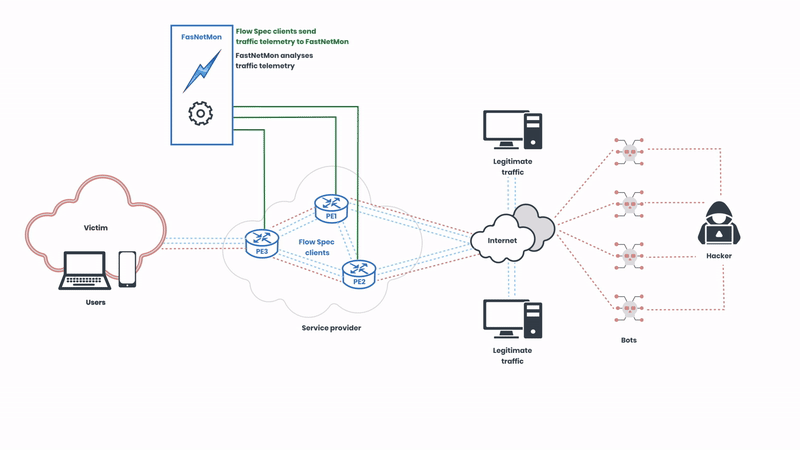
The hacker on the right side of the illustration initiates the attack and starts sending a high volume of traffic to the network. The network is under distress, but the source of the traffic can be hard to identify as the hacker is imitating legitimate internet traffic via a botnet. The hacker can send hundreds of gigabits of traffic in a matter of seconds, and therefore acting fast is crucial. Now, let’s observe how this attack can be mitigated with BGP Flow Spec:
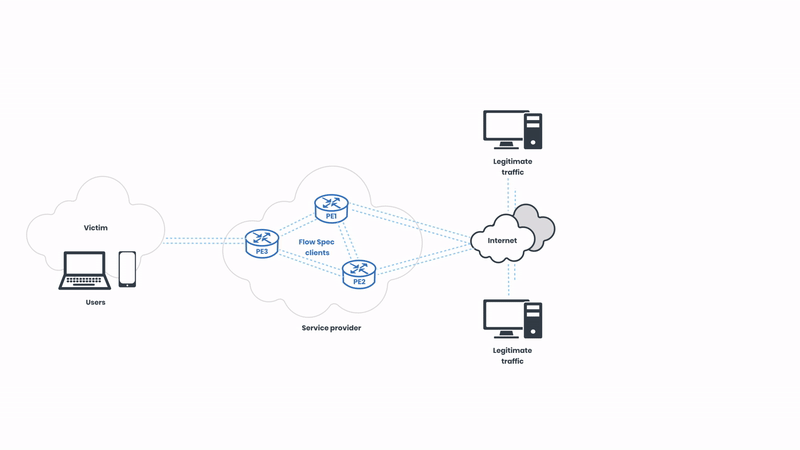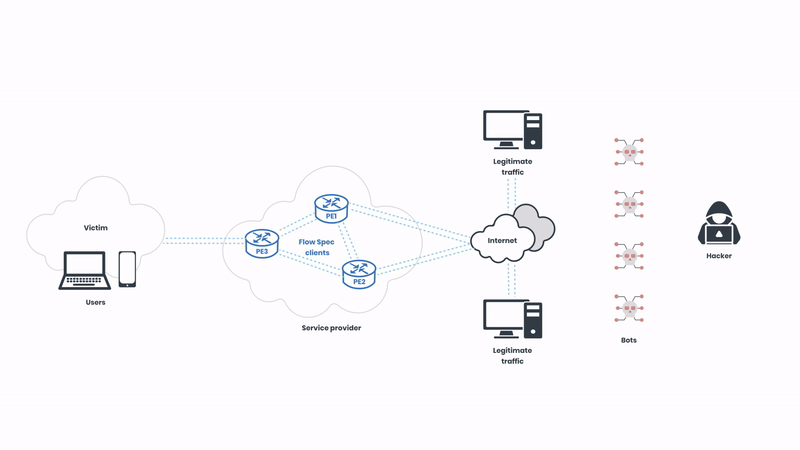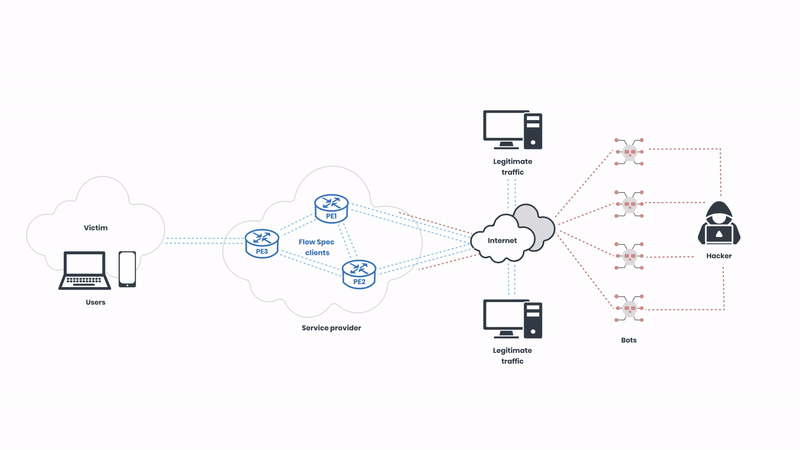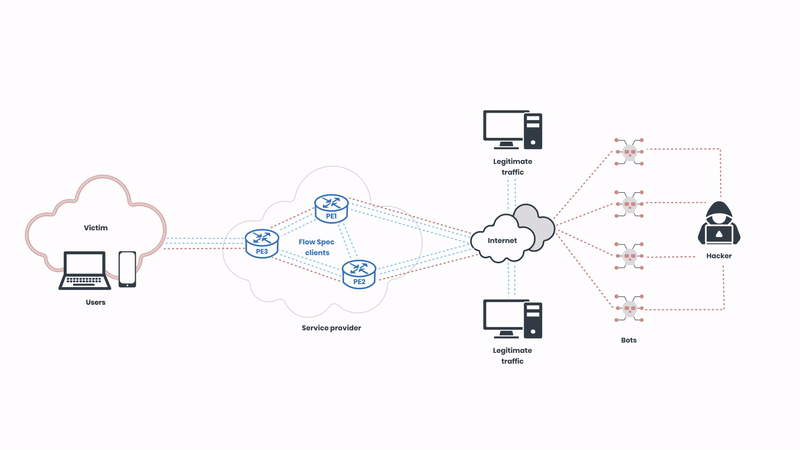
The Flow Spec clients of the service provider send traffic telemetry for analysis, and the network operators can create rules that specify detailed conditions under which traffic should be rate-limited or redirected. These rules are then distributed across the network in real-time, allowing for immediate response to emerging threats. In this illustration, the network operator is using FastNetMon to automatically analyse the telemetry. Next, let’s observe how the attack is mitigated:
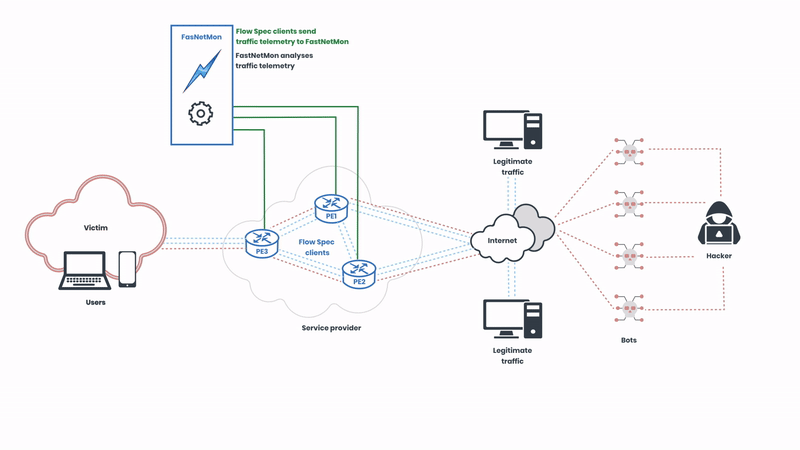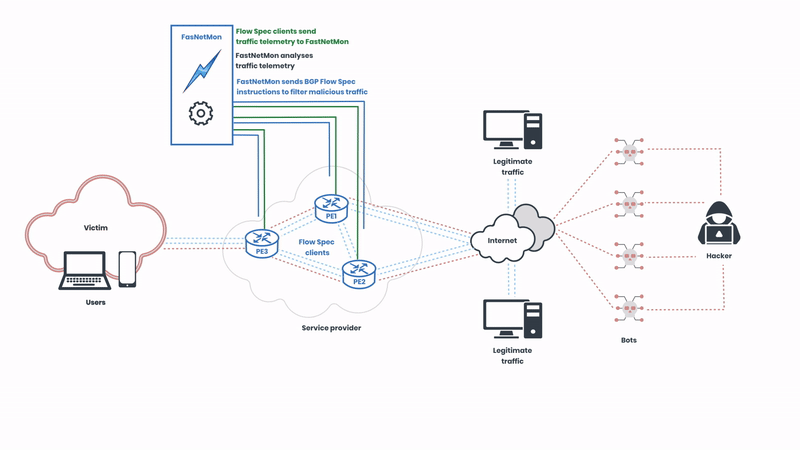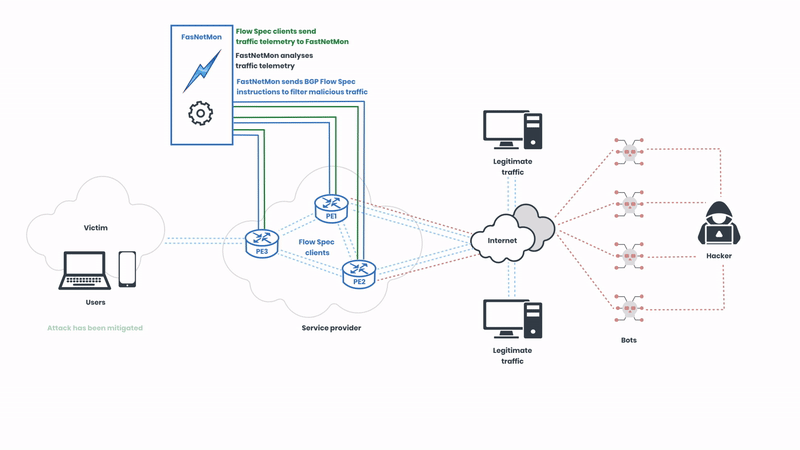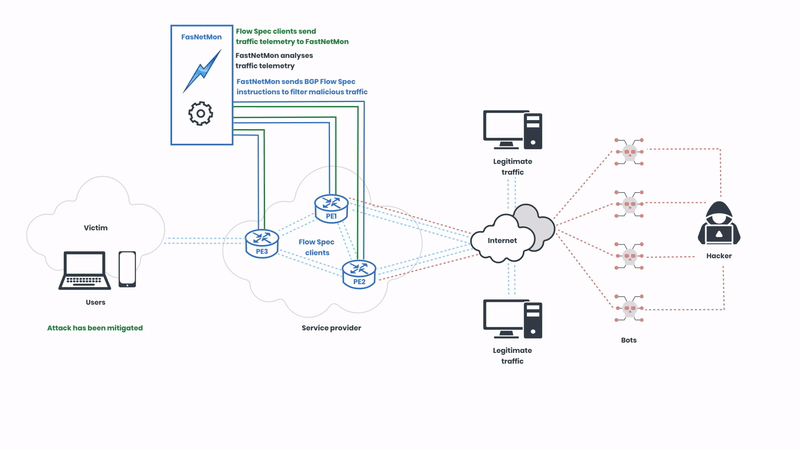
Here, we can observe FastNetMon sending BGP instructions to the Flow Spec clients to filter the malicious traffic. The protocol supports various actions such as traffic rate limiting, redirection, and filtering based on numerous attributes like IP addresses, ports, and packet types. This granularity ensures that only malicious traffic is mitigated, preserving normal network operations. The malicious traffic is detected in seconds, and the rules are deployed in real-time.
Vendor Support
The effectiveness of BGP Flow Spec in real-world applications depends significantly on vendor support. Major network equipment vendors including Cisco, Juniper, Huawei, Nokia, and Arista have implemented BGP Flow Spec in their devices, allowing network operators to deploy Flow Spec rules directly onto routers and switches.
These implementations vary in terms of the specific features and capabilities supported, and understanding these differences is crucial for network engineers when planning and deploying BGP Flow Spec solutions.
Conclusion
BGP Flow Spec represents a significant advancement in network traffic management and DDoS mitigation. It provides the capability to specify detailed traffic rules and rapidly distribute these rules across the network. BGP Flow Spec offers a powerful protocol to protect network resources from the growing threat of DDoS attacks, and FastNetMon provides the toolset for network operators to set up and manage their Flow Spec implementation.
About FastNetMon
FastNetMon delivers versatile DDoS detection software for companies at any scale. With extensive experience in the telecom, mobile, and cloud computing industries, we take pride in preventing DDoS attacks and protecting our customers’ networks to the highest standard.
Contact us at sales@fastnetmon.com