What can we learn from the alleged high-profile cyber attack?
Earlier this month, social media platform X (formerly Twitter) experienced a major DDoS attack that caused intermittent outages for users worldwide. While service was eventually restored, the real story began after the attack, when Elon Musk published claims about its origin.
Just weeks after the first large-scale DDoS attack, X faced another outage on March 30. The impact was again global, particularly for users of the X mobile app. According to the data, over 57% of users affected were using the app on iOS and Android, while others experienced issues accessing the platform via desktop. The latter outage has not yet been officially acknowledged by X’s technical team, which leaves room for speculation – is this another cyberattack or just platform instability?
In this article, DDoS professionals shed light on the reality of such claims and explain the realities and common misconceptions about DDoS attacks.
Where do DDoS attacks originate from?
Elon Musk published several posts about the incident, initially claiming that the attack was conducted by a coordinated group or even a nation-state with vast resources. Later, he claimed that a large proportion of the traffic came from Ukraine, insinuating responsibility.
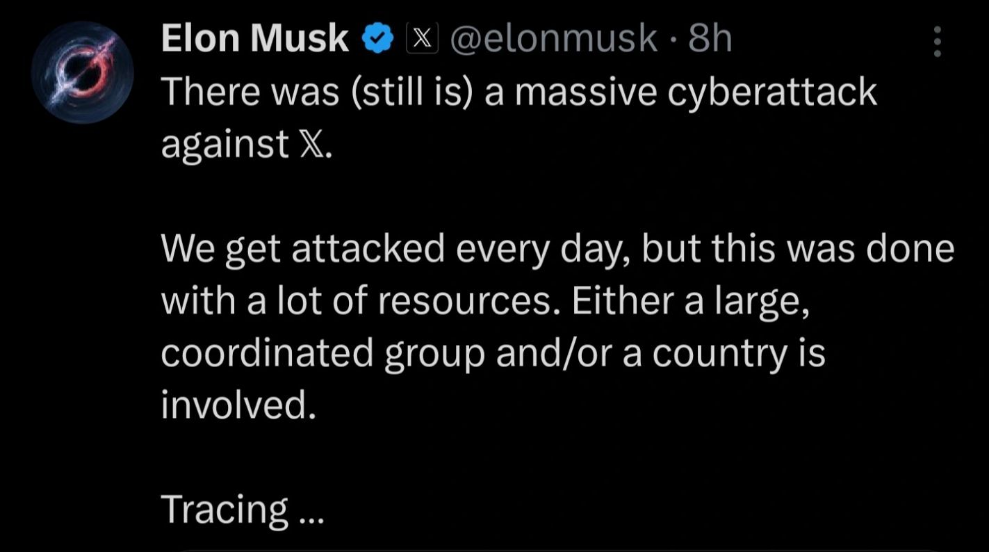
This statement was met with swift criticism from cybersecurity professionals across various news outlets. The reality is that attributing a DDoS attack, or any cyberattack, based on IP address alone is naive at best. Attackers systematically use VPNs, proxies, spoofing, and botnets to mask their origin. These tactics make it nearly impossible to say with certainty where an attack comes from — or who is responsible.
In general, the IPs used in a DDoS campaign do not belong to the attacker at all. They come from hijacked devices scattered across the globe: poorly maintained IoT equipment like security cameras or smart home devices, poorly maintained routers, printers, and more. Countries with large populations or a high number of internet-connected devices often appear overrepresented in DDoS traffic simply because there’s more opportunity for devices to be compromised – not because the attackers are necessarily located in those countries.
Attribution in this context is more art than science, and careless claims can cause more confusion than clarity. Additionally, attacks much more often originate from far less benign actors than nation-states’ coordinated cyberwar efforts. The overwhelming majority of attacks reportedly come from competitors or unhappy customers.
The risks of saying too much
When it comes to handling any cyberattack, sharing technical post-mortems in public can backfire. The same goes for DDoS attacks: It is very risky to disclose too many details — such as how the attack was conducted, how the malicious traffic was blocked, what tools and techniques were used, or where gaps were discovered. This may give the attackers a chance to regroup and come back better prepared.
We at FastNetMon are also well aware of this risk. While FastNetMon is an active news outlet for DDoS-related cybersecurity news, with a wealth of insider insight, we sometimes have to curb the information shared. Cybersecurity isn’t just about patching holes. It’s also about managing what you communicate, both internally and externally. Sometimes, silence is part of the strategy.
Claiming the blame for a DDoS attack
DDoS attacks are hard to trace because they are intentionally decentralised. Tens of thousands of devices can be used in a single attack. Some of these attacks are launched using DDoS-as-a-Service tools, which are increasingly easy to access. So-called ‘Stresser’ services are sold as legitimate testing tools, but ‘booter’ services are deliberately built to be used for disruption. These services are unfortunately very easily accessible, and at price points even regular consumers can afford. Technically, anyone could have paid for a booter service to initiate a DDoS attack towards X.
The larger, more high-profile attacks are often claimed by known groups of hackers, not individual actors. In X’s case, one such group, Dark Storm Team, claimed responsibility. Dark Storm Team is a pro-Palestinian hacker group that has been operating since late 2023. However, claims don’t always equal truth. Hacker groups are sometimes, quite controversially, seeking publicity for their actions and claiming unclaimed attacks to attract more attention and support for their hacktivist causes.
What can DDoS victims do to improve their defences?
Defence options against DDoS exist, but no single measure is foolproof. Much of the mitigation techniques depend on the exact attack surface, infrastructure, and hardware setup. What matters is layered defence that is well thought out for the specific use case — combining traffic monitoring, rate limiting, early detection, and lightning-fast automation to act before the network is overwhelmed with malicious traffic.
About FastNetMon
FastNetMon is a leading solution for network security, offering advanced DDoS detection and mitigation. With real-time analytics and rapid response capabilities, FastNetMon helps organisations protect their infrastructure from evolving cyber threats.


