A practical breakdown of DDoS attack vectors, built for network operators
When your NOC wallboard lights up red, you don’t have 5 seconds. And if you’re relying on manual triage at that point, it is a tough job.
Ideally, you’ve preloaded mitigation rules for the most common vectors. But when something new slips through, classification still matters. Knowing what kind of attack you’re seeing—and what response path to trigger—can make the difference between a minor incident and a major outage.
This guide acts as your mental model and checklist for exactly that moment. It helps turn reactive scrambling into repeatable, automatable playbooks.
In 2025, the attack surface is broader than ever. Cloudflare reported 7.3 Tbps / 4.8 Bpps network floods in Q2 2025, while Google weathered a 398 million RPS HTTP/2 Rapid Reset storm. The techniques are evolving—and so should your defence logic.
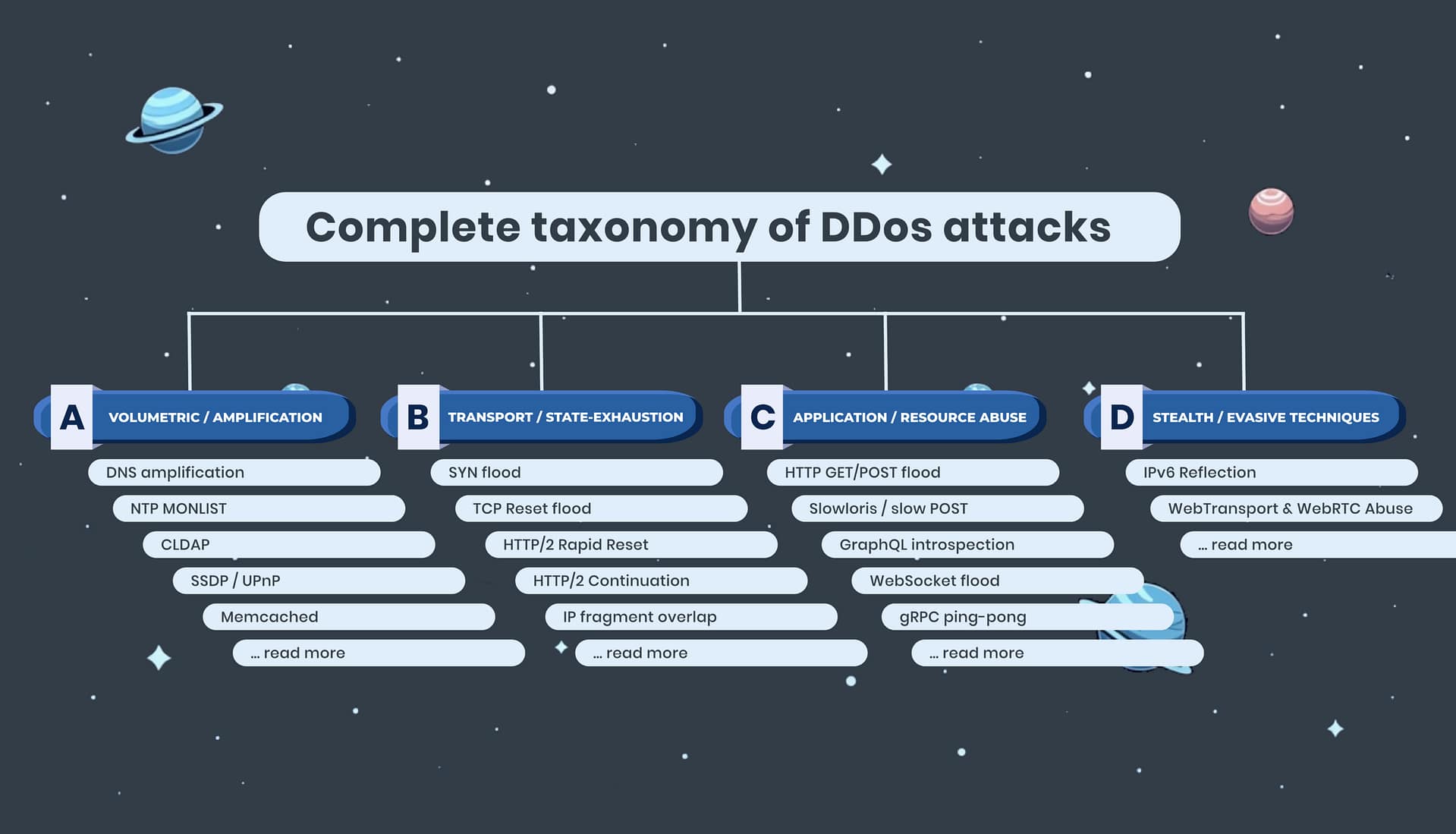
FastNetMon’s DDoS Taxonomy
We group attacks by what they try to break:
| Group | What it targets | Key question |
|---|---|---|
| A. Volumetric / Amplification | Links, NICs, routers | Will it fill my pipes? |
| B. Transport / State-Exhaustion | Firewalls, proxies, OS stacks | Will it kill my state tables? |
| C. Application / Resource Abuse | CPUs, databases, APIs | Will it burn my backend? |
| D. Stealth / Modulation Techniques | Detection heuristics | Will it evade thresholds? |
A. Volumetric & Amplification Attacks
Will it fill my pipes?
| Vector | Proto / Port | Typical Amp. | Record Size | Short Mechanics |
|---|---|---|---|---|
| DNS amplification | UDP/53 | ≤70× | 1.3 Tbps | Spoofed ANY/TXT to open resolvers |
| NTP MONLIST | UDP/123 | 200–500× | 400 Gbps | Server replies with 600 host list |
| CLDAP | UDP/389 | 56–70× | 70 Gbps | Conn-less LDAP reply |
| SSDP / UPnP | UDP/1900 | 20–30× | 112 Gbps | Spoofed M-SEARCH to IoT |
| Memcached | UDP/11211 | 10,000–51,000× | 1.7 Tbps | Cached payload dump |
| Jenkins discovery | UDP/3283 | 20–100× | Growing fast | Multicast reflection |
| RIPv1 | UDP/520 | 10–20× | 0.5 Tbps | Routing table spoof |
| QUIC broadcast | UDP/443 | 8–30× + CPU | Emerging | One Initial pkt → many workers |
| TCP middlebox refl. | TCP/80,443 | 2–75× | 11 Gbps | Proxy rejects reflected |
| TCP SYN-ACK refl. | TCP/* | 5–50× | Common | LB SYN-ACKs on spoofed SYNs |
| Smurf / Fraggle | ICMP / UDP/7 | 2–5× | Rare | Broadcast echo/reply |
Understanding Volumetric Attacks
Volumetric and amplification-based DDoS attacks are designed to consume network bandwidth, often overwhelming routers, switches, and firewalls before the traffic even hits your application layer. These attacks exploit open or misconfigured servers to amplify small requests into massive payloads directed at a victim.
Classic UDP-based amplifiers such as DNS, NTP, and CLDAP are still widely abused due to their high amplification factors and continued presence in legacy systems. More recent additions like Memcached offer staggering amplification ratios, with single-packet queries returning hundreds of kilobytes.
A newer trend is the exploitation of protocols that were not traditionally seen as reflective, such as QUIC. By abusing initial handshake behavior or load-balancer misconfigurations, attackers can trigger wide amplification patterns that include CPU burn, not just bandwidth floods.
Carpet-bombing is an increasingly common stealth technique. Instead of flooding a single IP, attackers distribute packets evenly across entire IP blocks—such as a /24—making per-host traffic appear benign, while the total volume exceeds hundreds of Gbps. This method bypasses many per-IP detection thresholds and demands broader visibility to detect.
The key defence here is network-layer filtering using BGP Flowspec, access control lists (ACLs), and upstream scrubbing providers. Detection must go beyond absolute volume and account for protocol anomalies and dispersion patterns.
To understand volumetric and amplification attacks in more detail, read this complete guide.
B. Transport & State-Exhaustion Attacks
Will it kill my firewalls or proxies?
| Attack | Layer | CVE / Year | Peak Seen | Core Abuse |
|---|---|---|---|---|
| SYN flood | 3/4 | — | 4.2 Tbps | Half-open queue exhaustion |
| TCP Reset flood | 4 | — | 11 Mpps | Spoofed RST tears down sessions |
| HTTP/2 Rapid Reset | 7 | 2023 | 398M rps | RST_STREAM spam to hold conn |
| HTTP/2 Continuation | 7 | 2024 | PoC → OOM | Infinite CONTINUATION frames |
| QUIC-loris (Initial flood) | 4/7 | 2025 | High CPU | 0-RTT handshake loops |
| gRPC SETTINGS/HPACK | 7 | 2019–2024 | App stall | SETTINGS loop + header abuse |
| IP fragment overlap | 3 | — | 80 Gbps | Reassembly buffer overflow |
| Pulse-wave modulation | meta | 2024 | 300–350 Gbps | On/off bursts defeat baselines |
Understanding State-Exhaustion Attacks
These attacks exploit the asymmetric cost of maintaining connection state. A small number of malicious packets can consume disproportionately large amounts of CPU, memory, or table entries in firewalls and proxies.
SYN floods remain a classic and effective attack by filling up the half-open TCP connection queue. Meanwhile, TCP Reset floods tear down legitimate sessions by spoofing RST packets, disrupting user experience without consuming significant bandwidth.
State-exhaustion attacks have evolved to layer 7, with HTTP/2 being the prime target. The Rapid Reset vulnerability, for instance, enables a client to reuse a single TCP connection to generate millions of stream resets, effectively stalling backend thread pools while staying under protocol stream limits.
QUIC and gRPC are also vulnerable, often by abusing handshake flows or metadata processing logic. These attacks tend to result in CPU spikes or thread starvation in proxies and load balancers.
Pulse-wave modulation—a modulation technique where attackers alternate between bursts and silence—makes these attacks harder to detect using baseline rate thresholds. For mitigation, consider stateless defenses such as SYN cookies, QUIC retry tokens, header-size caps, and connection rate limits per source IP.
To understand transport and state exhaustion attacks in more detail, read this complete guide.
C. Application-Layer & Low-and-Slow Attacks
Will it burn my CPUs or databases?
| Vector | Metric | Trick | Target Environment |
|---|---|---|---|
| HTTP GET/POST flood | Up to 200M rps | Bot swarms with cache-bust params | E-commerce, fintech |
| Slowloris / slow POST | <1 Mbps stalls | Partial headers/bodies | Apache, Nginx |
| GraphQL introspection | 1–10k rps | 1000+ directives or recursion | API backends |
| WebSocket flood | 100k conn/s | Chat open + discard frames | Gaming, social |
| gRPC ping-pong | Few k rps | Keep-alive + metadata loop | Microservice meshes |
| Login/cache-bust spray | 10–40k rps | Unique queries bypass CDN | SaaS, portals |
| Prefix-scatter L7 | 1–2k rps/IP | Same req across /24 | Hosting infra |
Understanding Application-Layer Abuse
Layer-7 attacks focus on CPU, memory, and application logic, often flying under the radar of volumetric detection systems. These vectors abuse HTTP, WebSocket, GraphQL, and gRPC to exhaust server resources.
The simplest form is an HTTP GET or POST flood, often using browser-like bots with randomised headers or query strings that bypass caching layers. Slowloris-style attacks consume sockets by sending partial HTTP headers or bodies at a trickle.
Modern APIs introduce new risks. GraphQL introspection queries can trigger deep recursion with minimal input. gRPC SETTINGS floods and header compression loops are capable of stalling or crashing backend services even with low RPS.
Layer-7 vectors are particularly dangerous due to their low bandwidth profile, often staying under traditional detection thresholds. Furthermore, CDN and WAF layers are not immune, especially when attackers vary queries to force cache misses.
To mitigate, deploy dynamic rate-limiting per endpoint, enable CAPTCHA and authentication challenges, use circuit breakers, and enforce schema/query depth limits on APIs.
D. Emerging and Evasive Techniques
Several trends in DDoS evolution demand attention:
- IPv6 Reflection: Over 3,500 ASes expose v6 amplifiers. Source validation (SAV) is lacking in over 60% of them.
- WebTransport & WebRTC Abuse: TURN relays can reflect traffic with 10–15× amplification. Early PoCs already exist.
- AI-Powered Bots: Attackers now emulate real browser behavior—jitter, headers, cookie use—making them harder to filter.
Modulation techniques such as carpet-bombing and pulse-wave attacks further complicate detection. These methods spread load across the address space or time to evade traditional alerts based on volume or sustained rates.
Detection systems must evolve to correlate traffic patterns across subnets, monitor time-based anomalies, and analyse protocol behaviour at the application layer.
How to Use This Taxonomy in Real Incidents
| Symptom | Likely Vector | Lookup Table |
|---|---|---|
| Huge PPS on one port | Amp/reflection | Table A |
| High conn/sec, low bandwidth | State exhaustion | Table B |
| Backend 500s, normal NetFlow | Application abuse | Table C |
Mitigation Matchups:
| Attack Class | Mitigation Strategy |
|---|---|
| Volumetric | BGP Flowspec, scrubbing, ACLs |
| State Exhaustion | Protocol hardening (SYN cookies, stream caps) |
| Application | Dynamic rate-limiting, query caps, circuit breakers |
Detection systems should be updated with heuristics for:
- Carpet-bombing: Multi-IP floods per /24 or /22
- Pulse-wave: High-frequency burst/idle cycles
Summary: Know the Beast, Load the Bullet
- Reflection attacks are evolving—QUIC and TCP are viable amplifiers now.
- Protocol design flaws (e.g., HTTP/2, gRPC) drastically increase DDoS efficiency.
- Low-and-slow vectors remain potent, especially against APIs.
- IPv6 will be the next hot zone—start enabling uRPF and source validation today.
Stick this post on your team wiki. When the next flood hits, you’ll know what you’re facing—and exactly how to respond.
Happy packet herding!
About FastNetMon
FastNetMon is a leading solution for network security, offering advanced DDoS detection and mitigation. With real-time analytics and rapid response capabilities, FastNetMon helps organisations protect their infrastructure from evolving cyber threats.
For more information, visit https://fastnetmon.com