How bandwidth-focused DDoS campaigns work—and why they’re still effective at scale
Volumetric DDoS attacks remain one of the most common and disruptive forms of denial-of-service activity across the internet. Despite evolving tactics, the core objective is the same: exhaust the network capacity of a target by overwhelming it with traffic. This article explores how volumetric attacks work, how amplification plays into them, and what defenders should understand when detecting and mitigating these threats.
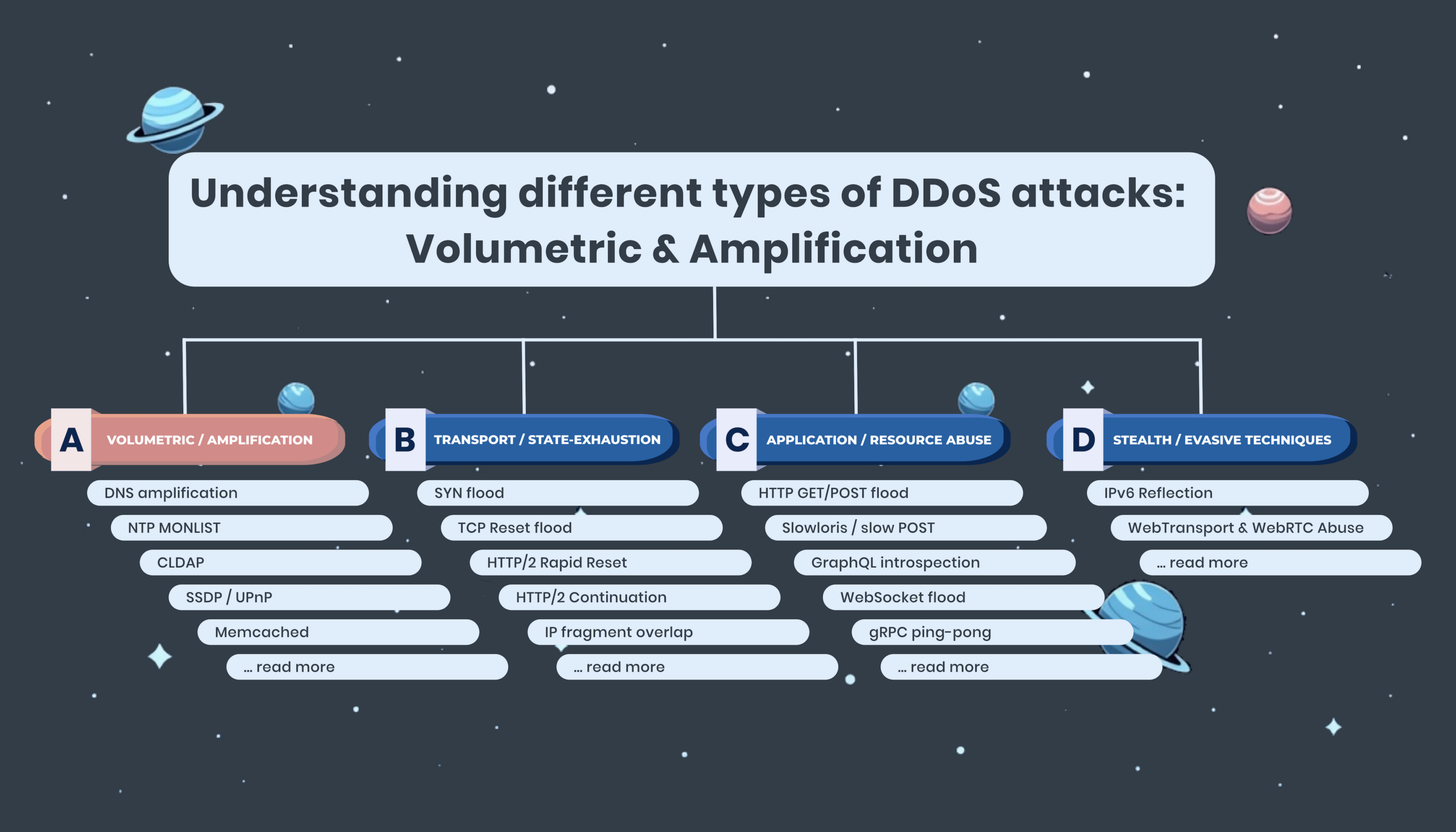
This article is part of a longer series of articles about different types of DDoS attacks. If you’re new here, have a look at our DDoS taxonomy to start with a solid understanding of how volumetric and amplification attacks fit into the wider DDoS attack landscape.
What Is a Volumetric DDoS Attack?
A volumetric DDoS attack aims to consume the bandwidth of the target system—or its upstream providers—by sending overwhelming amounts of data. These attacks are designed to flood the network layer (Layer 3) and transport layer (Layer 4), effectively clogging all available capacity.
This approach doesn’t try to exploit application vulnerabilities. Instead, it focuses on brute-force disruption of internet connectivity.
How Volumetric Attacks Work
At their core, volumetric attacks use large volumes of packets—often from distributed sources—to saturate links and infrastructure. The most common mechanisms include:
UDP Flood
A UDP flood sends large numbers of User Datagram Protocol packets to random or targeted ports on the victim’s IP address. Because UDP is stateless, the server either processes the traffic or responds with ICMP Destination Unreachable messages, consuming additional resources.
ICMP Flood (Ping Flood)
This method sends a large number of ICMP Echo Request (ping) packets, often targeting infrastructure or endpoints directly. Some variants use broadcast addresses to generate amplified ICMP replies to the spoofed victim IP.
TCP-Based Floods
While not as common in pure volumetric campaigns, TCP SYN floods and RST floods can be used to consume state on connection tables, especially if combined with other tactics.
Key Characteristics
Here are some of the common characteristics of volumetric attacks:
| Feature | Description |
|---|---|
| Attack Goal | Maximize traffic volume to saturate bandwidth |
| Measurement | Typically in Gbps or packets per second (pps) |
| Common Protocols | UDP, ICMP, TCP SYN |
| Botnet Requirement | Usually requires high-scale distributed traffic sources |
| Mitigation Challenge | Volume alone can overwhelm links before deeper filtering can take place |
Amplification: A Subclass of Volumetric Attacks
Amplification attacks are a more efficient variant of volumetric DDoS. Rather than sending large volumes directly, attackers send small, spoofed requests to vulnerable third-party servers, which then respond with much larger replies to the target.
This allows an attacker to multiply their outbound bandwidth—turning a small investment into a massive flood.
How Amplification Works (Step-by-Step)
- Spoofed Source: Attacker sends a forged request with the victim's IP address.
- Open Service Responds: Vulnerable server replies with a much larger response.
Victim Flooded: The response is directed to the victim, consuming their bandwidth.
Common Amplification Vectors
Here are some of the most common amplification vectors explained, with their typical amplification ratio:
| Protocol/Service | Vector Description | Amplification Ratio (Typical) |
|---|---|---|
| DNS | Queries (e.g., ANY/TXT) sent to open resolvers | 30x–100x |
| NTP | Abuse of the monlist command | 20x–200x |
| Memcached | Spoofed queries result in multi-megabyte responses | Up to 50,000x |
| CLDAP / SSDP | Lightweight protocols with poor access controls | 50x–70x |
These services are often exposed due to misconfiguration or legacy deployments. Their amplification ratios depend on response size vs request size.
Real-World Example: DNS Amplification
A typical DNS amplification attack might involve:
- Sending a 60-byte ANY-type DNS query to an open resolver, spoofing the victim’s IP.
- The resolver responds with a 4,000-byte DNS response.
- Amplification ratio: ≈ 67×.
With just 1 Gbps of spoofed queries, an attacker could generate 67+ Gbps of inbound traffic directed at the victim.
Volumetric vs Amplification: Key Differences
It’s important to note: all amplification attacks are volumetric, but not all volumetric attacks involve amplification. Below are some of the key technical differences listed.
| Characteristic | Volumetric Attack | Amplification Attack |
|---|---|---|
| Traffic Source | Direct from attacker (often via botnet) | Reflected from third-party servers |
| Spoofing Required | Optional | Required |
| Efficiency | Low (relies on raw scale) | High (relies on protocol weaknesses) |
| Detection Clues | Large traffic volumes, many sources | High-volume responses from known reflectors |
| Mitigation Approach | Rate-limiting, filtering, blackholing | Reflection-aware filtering, IP reputation, Flowspec rules |
Detection and Defence: What Matters Most
To effectively mitigate these attacks in real time, defenders need:
- Protocol and Port-Level Visibility: Identify abnormal surges in traffic types (e.g., UDP/123, UDP/53). Have a look at FastNetMon’s network visibility tools here.
- Per-IP and Per-Prefix Thresholds: Customise detection rules for bandwidth, packet rate, and flow count per asset. Read our guide on setting thresholds here.
- Anomaly Detection: Spot deviations from baseline traffic—especially relevant for low-and-slow or spread-out (carpet bombing) attacks.
- Reflection Pattern Awareness: Recognise common amplification signatures (e.g., many unsolicited DNS responses).
- Automated Mitigation Tools: BGP blackholing, Flowspec filtering, and integration with inline scrubbing or firewalls. Have a look at FastNetMon’s stack here.
Fast detection and precise reaction are critical. Bandwidth exhaustion can happen in seconds once a volumetric campaign starts.
Summary
Volumetric and amplification attacks continue to dominate the DDoS landscape due to their simplicity, scalability, and ability to take networks offline without exploiting application logic.
- Volumetric attacks rely on high packet volume to flood links directly.
- Amplification attacks abuse misconfigured third-party services to dramatically increase attack size.
- A strong DDoS defence strategy requires real-time traffic analytics, dynamic thresholds, and automated mitigation methods that respond in seconds.
Want a full understanding of different DDoS attack types and how to defend agains them? Continue reading our article for a full DDoS classification.
About FastNetMon
FastNetMon is a leading solution for network security, offering advanced DDoS detection and mitigation. With real-time analytics and rapid response capabilities, FastNetMon helps organisations protect their infrastructure from evolving cyber threats.
For more information, visit https://fastnetmon.com