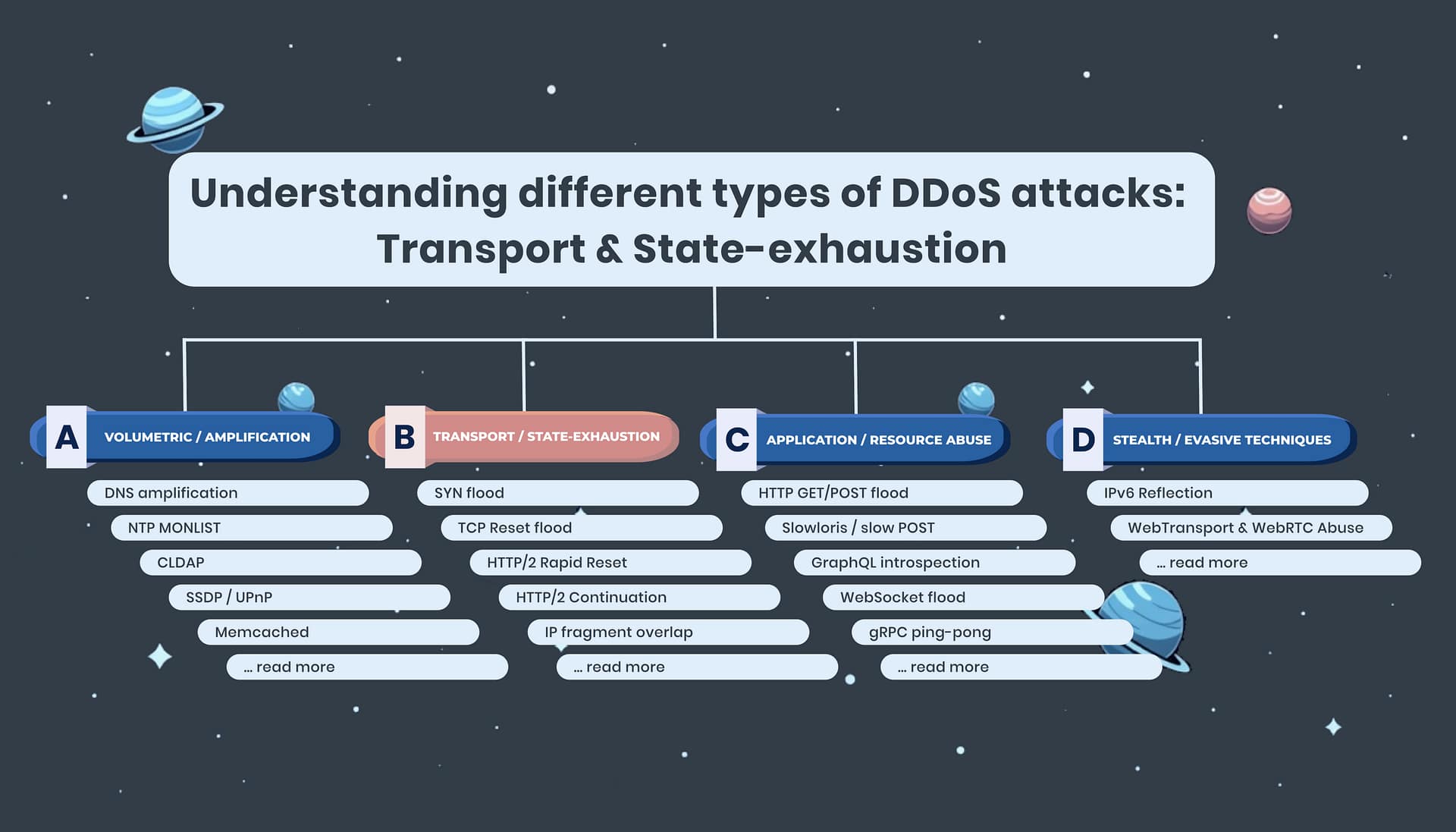
How connection state exhaustion attacks threaten your firewalls and proxies
Transport and state-exhaustion DDoS attacks represent a growing and sophisticated category of denial-of-service threats targeting the resource limitations of network infrastructure. Instead of flooding bandwidth, these attacks exploit the costly state and CPU resources needed to manage connections and sessions in firewalls, proxies, load balancers, and servers. This article breaks down how these attacks work, their evolving vectors, and key considerations for detection and mitigation.
This article is part of a longer series about different types of DDoS attacks. If you’re new here, start with our DDoS taxonomy to understand how transport and state-exhaustion attacks fit within the broader DDoS landscape.
What are Transport and State-Exhaustion Attacks?
Transport and state-exhaustion attacks are closely related but distinct classes of DDoS threats targeting connection management rather than bandwidth:
- Transport Attacks focus on abusing transport-layer protocols like TCP and QUIC. They disrupt connection establishment, teardown, or handshake processes. Examples include SYN floods and spoofed TCP reset floods.
- State-Exhaustion Attacks target the stateful resources that devices allocate for connection tracking, such as memory, CPU, and connection tables. By creating numerous half-open, stalled, or malformed connections, these attacks deplete critical infrastructure capacity.
Though interrelated (transport attacks often cause state exhaustion), the distinction clarifies attack mechanics and informs mitigation strategies.
Why Transport & State-Exhaustion Attacks Matter
Unlike volumetric floods that overwhelm bandwidth pipes, these attacks exploit the asymmetric cost of connection management. Small volumes of malicious traffic can trigger disproportionate resource consumption in stateful devices like firewalls, proxies, and application servers, leading to outages or degraded service.
These attacks can be stealthier and more complex to detect, as they may generate moderate traffic while causing an outsized impact by exhausting CPU, memory, or connection tables.
Common Attack Vectors and Their Impact
In the table below, we summarise some of the most common transport and state-exhaustion attack vectors observed in the wild. For each, we highlight the targeted protocol layer, notable peak attack metrics, and the core resource or mechanism being exploited. This overview provides a quick reference to understand the diversity and impact of these threats.
| Attack Type | Layer | Description | Notable Peak Impact | Resource Targeted |
|---|---|---|---|---|
| SYN Flood | 3/4 | Floods half-open TCP connections by sending SYN packets without completing handshake | 4.2 Tbps seen | Half-open TCP connection queue |
| TCP Reset Flood | 4 | Spoofs TCP RST packets to tear down legitimate sessions prematurely | 11 Mpps observed | Session teardown |
| HTTP/2 Rapid Reset | 7 | Sends excessive RST_STREAM frames to stall backend processing | 398M resets per second (2023) | Backend thread pool exhaustion |
| HTTP/2 Continuation | 7 | Sends endless CONTINUATION frames without END_HEADERS flag, causing memory and CPU exhaustion | Proof of concept (2024) | Memory overflow, CPU spike |
| QUIC-Loris Initial Flood | 4/7 | Abuses QUIC 0-RTT handshake loops causing high CPU load | High CPU load (2025) | CPU exhaustion during handshake |
| gRPC SETTINGS/HPACK | 7 | Sends continuous SETTINGS frames and abuses header compression to stall applications | Ongoing since 2019–2024 | Application stall |
| IP Fragment Overlap | 3 | Sends overlapping IP fragments to exhaust reassembly buffers | 80 Gbps observed | Buffer overflow |
| Pulse-Wave Modulation | Meta | Alternates bursts and silence to evade detection | 300–350 Gbps bursts (2024) | Evasion of baseline detection |
How These Attacks Work: Transport vs. State Exhaustion
- Transport attacks like SYN floods overwhelm the TCP handshake process by flooding servers with SYN packets, leaving many half-open connections that consume resources.
- TCP Reset floods use spoofed RST packets to abruptly terminate legitimate connections, disrupting service with low bandwidth.
- State-exhaustion attacks at Layer 7 abuse protocol features to force servers and proxies into high CPU or memory consumption. For example, HTTP/2 Rapid Reset floods generate massive stream resets that stall backend threads.
- QUIC-Loris exploits incomplete QUIC handshakes to spike CPU usage on proxies.
- gRPC abuses SETTINGS frames and header compression to exhaust application processing power.
- Pulse-wave modulation alternates high attack bursts and silence to evade rate-based anomaly detection.
Real-World Examples
- The 2023 HTTP/2 Rapid Reset attack generated nearly 400 million stream resets per second, overwhelming backend servers without breaching TCP connection limits.
- QUIC-Loris, discovered in 2025, showed how QUIC handshake loops can cause high CPU usage on proxies, leading to denial of service.
- Classic SYN floods have reached peaks of multiple terabits per second and remain a major vector, often combined with amplification for scale.
Key Differences Between Transport and State-Exhaustion Attacks
To better understand how transport-layer attacks differ from state-exhaustion attacks, the table below outlines their key characteristics side-by-side.
| Aspect | Transport Attacks | State-Exhaustion Attacks |
|---|---|---|
| Primary Target | Transport protocols (TCP, QUIC) | Stateful device/application resources |
| Attack Mechanism | Disrupting connection setup or teardown | Consuming memory, CPU, or state tables |
| Traffic Volume | Moderate to high | Moderate but resource-intensive |
| Detection Difficulty | Moderate (signatures possible) | High (behavioral/anomaly detection) |
Mitigation Strategies for Transport and State-Exhaustion Attacks
Transport and state-exhaustion DDoS attacks target the resource-intensive connection and session management mechanisms in network devices and servers. Mitigating these sophisticated attacks requires a layered approach combining network-level defences, protocol hardening, and application-aware protections.
Network-Level Defenses
- Flow-Based Anomaly Detection: Tools like FastNetMon leverage NetFlow, IPFIX, and sFlow telemetry to monitor connection rates, session counts, and protocol-specific anomalies. Customizable thresholds enable early detection of unusual spikes indicative of SYN floods, TCP reset floods, or HTTP/2 rapid resets.
- Automated Mitigation: FastNetMon supports integration with network infrastructure to trigger reactive measures such as BGP blackholing or BGP Flowspec filtering. These actions help drop attack traffic upstream, reducing the load on firewalls and proxies.
- Rate Limiting and Connection Controls: Implementing per-IP connection limits and request rate caps at the network edge reduces the risk of state table exhaustion.
Protocol and Application Hardening
- Stateless TCP Defences: Techniques like SYN cookies prevent resource allocation until TCP handshakes are completed, effectively mitigating SYN flood attacks.
- QUIC and HTTP/2 Protections: Enforcing frame size limits, connection limits, and retry token usage helps prevent abuse of modern protocols vulnerable to state exhaustion.
- Server and Proxy Configuration: Tuning timeout values, limiting simultaneous connections per client, and monitoring for suspicious HTTP/2 or gRPC frame patterns improve resilience against higher-layer state attacks.
Application-Layer Protections
While FastNetMon excels at network-level detection and mitigation, defending against state-exhaustion attacks targeting application servers and proxies often requires specialised application-layer defences, including:
- Application-specific rate limiting and challenge-response mechanisms.
- Web Application Firewalls (WAFs) with protocol-specific filtering.
- Deep packet inspection and behavioural analytics.
Conclusion
Transport and state-exhaustion DDoS attacks exploit connection management weaknesses and resource limitations rather than raw bandwidth. Their increasing sophistication at Layer 7 demands layered defence strategies combining stateless filtering, rate limiting, anomaly detection, and infrastructure robustness.
Want a full understanding of different DDoS attack types and how to defend against them? Continue reading our full DDoS taxonomy article to explore the entire landscape of attacks and defence techniques.
About FastNetMon
FastNetMon is a leading solution for network security, offering advanced DDoS detection and mitigation. With real-time analytics and rapid response capabilities, FastNetMon helps organisations protect their infrastructure from evolving cyber threats.
For more information, visit https://fastnetmon.com