Welcome to our Network Engineering Community News!
Hi from FastNetMon! September has been anything but quiet: record-scale DDoS attacks, new botnets, and plenty of network security updates kept us busy. In this issue, we’re sharing a practical telemetry guide, recapping our recent webinar, and bringing news from RONOG 10. And as usual, we're rounding up the latest DDoS news you don’t want to miss. Enjoy!
Want this letter straight to your inbox? Sign up to our monthly Network Engineering Community News
here.
FastNetMon detects a record scale 1.5Gpps attack
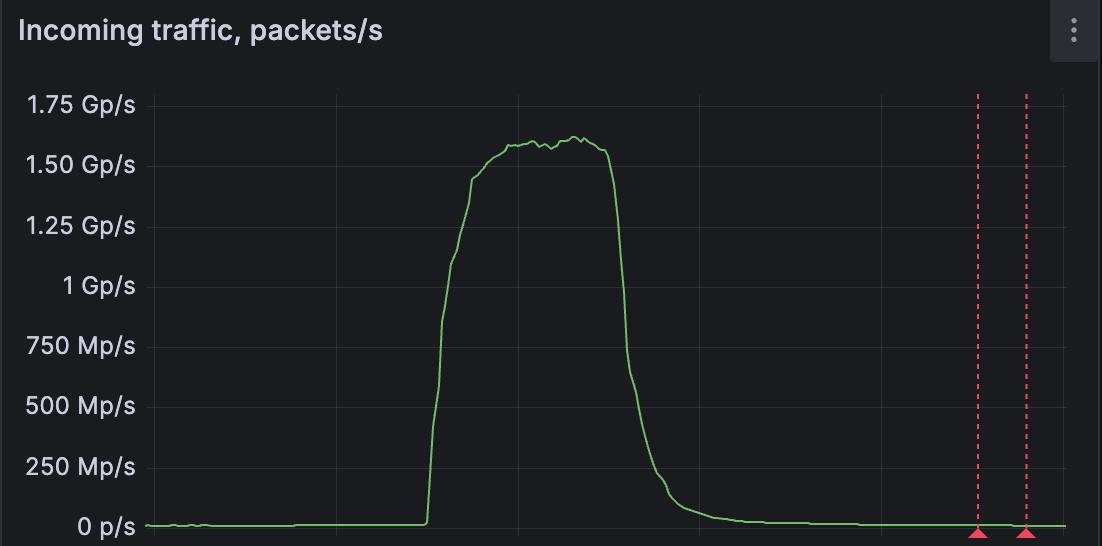
Earlier this month, FastNetMon picked up one of the largest DDoS attacks ever seen in the wild—1.5 billion packets per second at peak.
Numbers that big show how today’s attackers are pushing networks harder than ever and forcing defences to react in real time.
The story made waves across the industry:
- BleepingComputer: “The attack originated from thousands of IoTs and MikroTik routers, and it was mitigated by FastNetMon, a company that offers protection against service disruptions.”
- The Register: “A DDoS mitigation provider was given a taste of the poison it tries to prevent, after being smacked by one of the largest packet-rate attacks ever recorded.”
- SC Media: “Threat actors have launched a distributed denial-of-service attack peaking at 1.5 billion packets per second against an unnamed European DDoS scrubbing vendor.”
- Cybersecurity News: “The malicious traffic was primarily a UDP flood launched from compromised customer-premises equipment (CPE), including IoT devices and routers, across more than 11,000 unique networks worldwide.”
Webinar Recap: FastNetMon & Inter.link on Network Threat Landscape 2025
Earlier this month, FastNetMon joined forces with Inter.link for a live panel diving into the current network threat landscape.
Pavel Odintsov and Ciprian Abaseaca unpacked the latest DDoS trends, from record-breaking attacks like the recent 1.5 Gpps assault to the emergence of highly accessible botnets that were once only within reach of state actors. Hear them out on how detection and mitigation work hand-in-hand to keep networks running smoothly, offering practical insights for engineers and security teams alike.
If you missed the live session, the full discussion is now available on YouTube - catch the key insights and strategies straight from the experts.
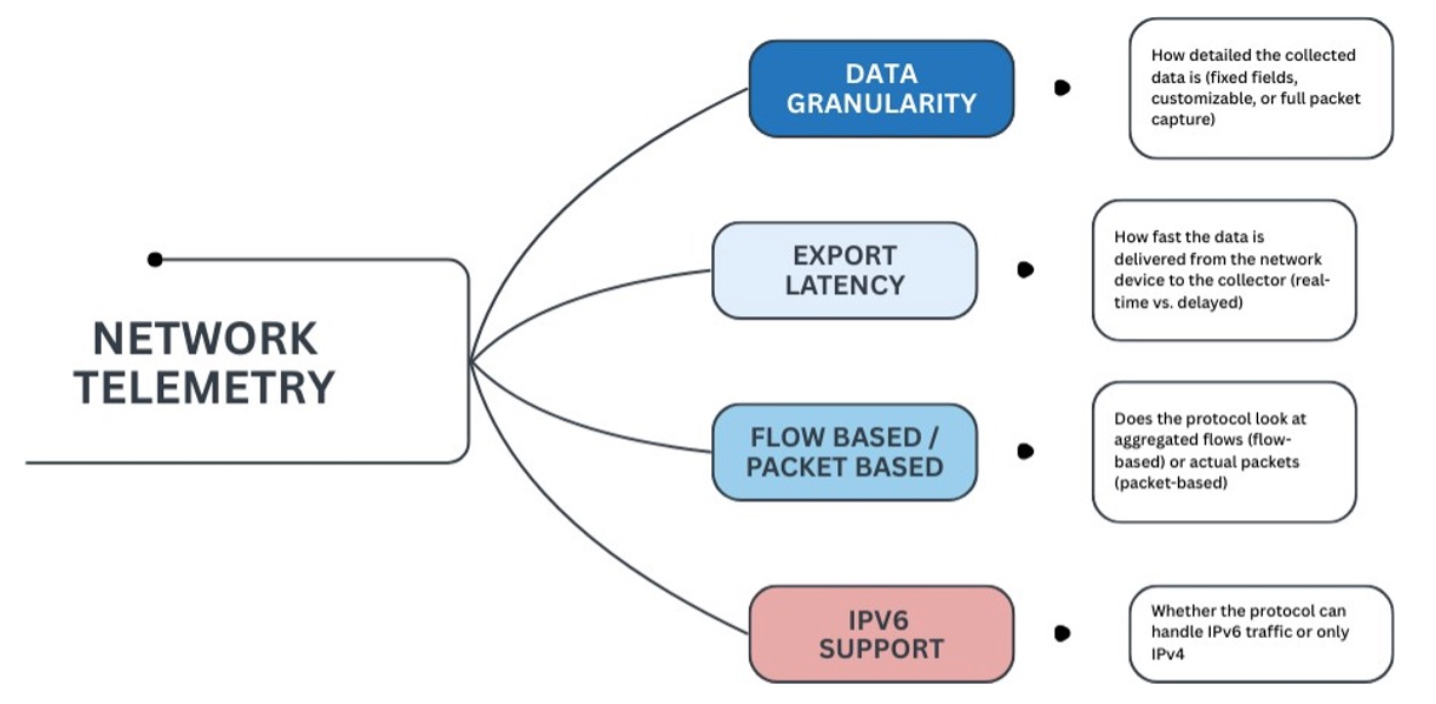
LACNIC ft. Pavel Odintsov: Making sense of network telemetry
In his latest blog featured on LACNIC, our CTO Pavel Odintsov walks readers through network telemetry, breaking down flow-based and packet-based approaches in a way that’s easy to follow.
Whether you’re monitoring traffic, spotting anomalies, or planning incident responses, this guide gives practical tips to help network engineers and operators make sense of the data that matters most.
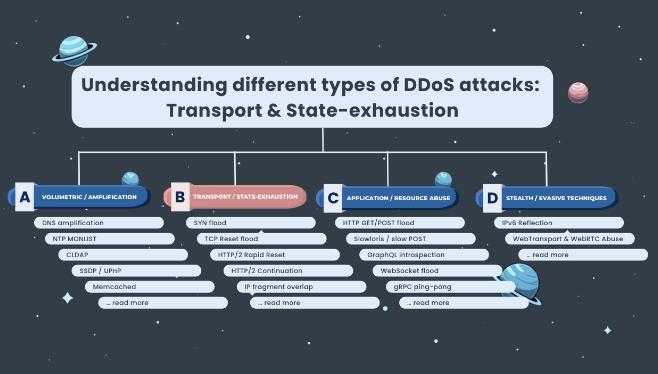
DDoS Taxonomy
DDoS attacks aren’t all the same, and treating them as if they are often leads to poor defences.
In this guide, you'll find every major DDoS attack vector, from floods at L3/L4 to the more complex L7 patterns, and explain how they work in practice.
It’s a practical taxonomy you can use to better understand, detect, and mitigate real-world attacks.
From RONOG 10: 2025 DDoS patterns, tips and insights

We were at RONOG 10, catching up with the network engineering community and sharing insights on the latest DDoS trends.
Virgil from our team presented on attack patterns, mitigation strategies, and what operators should watch for in 2025. While we’re still putting together a full event recap, you can check out the slides from the presentation to get the key takeaways.
Industry News
Here are some interesting industry takes and major DDoS incidents you should know about. Enjoy the reading!
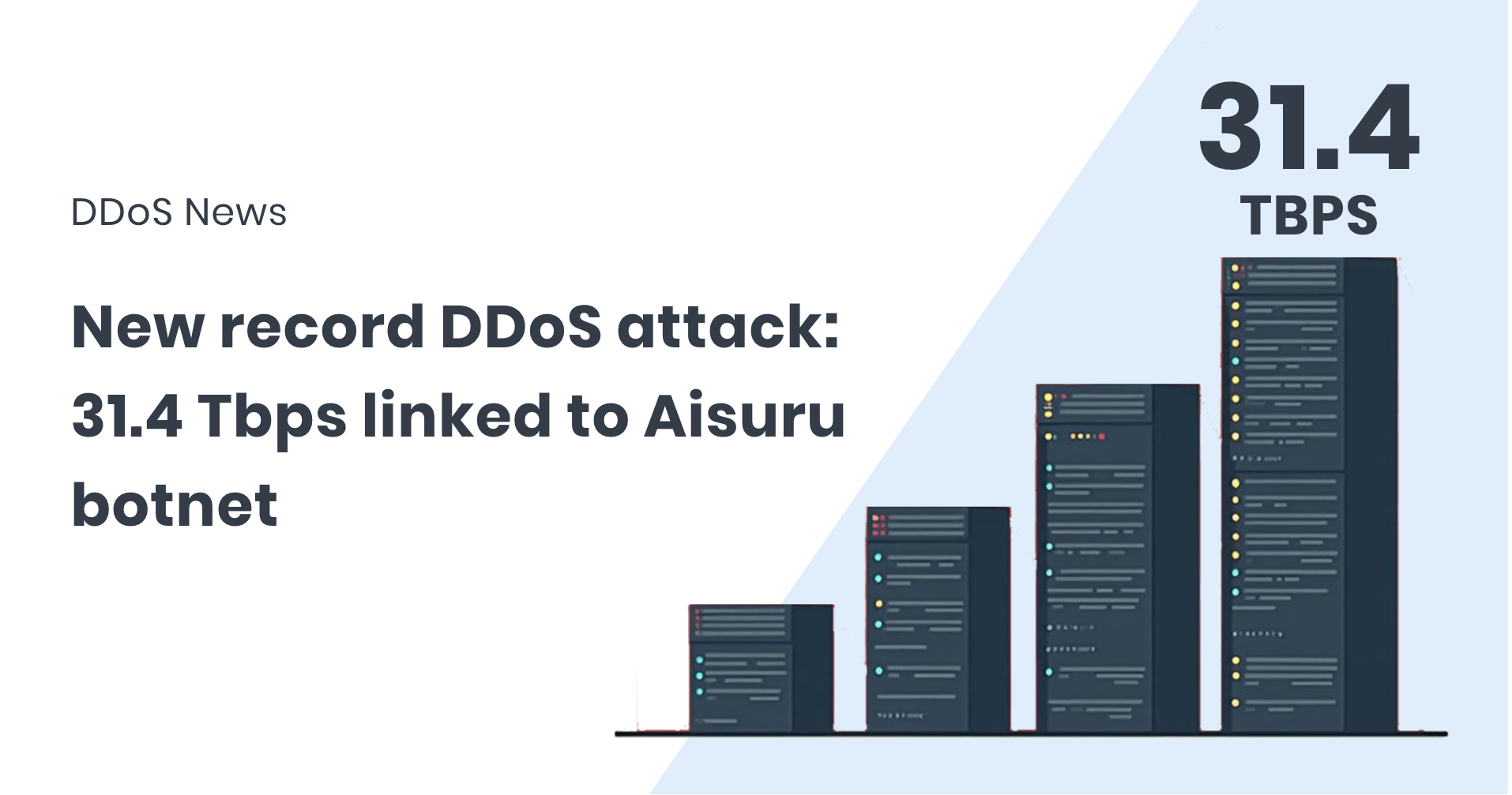
The bar just moved again. Attack volumes continue to hit new highs, with a flood peaking at 22.2Tbps. How can networks withstand traffic levels once thought impossible? Find details here.
FastNetMon caught one of the most intense packet-rate assaults ever observed, measuring 1.5 billion packets every second. How do attackers push packet floods to extremes? Read here.
Arch Linux confirmed that a week-long DDoS assault hampered its core infrastructure and mirrors. Open-source platforms, despite their resilience, are not immune to persistent disruption. More info here.
Cambridge’s latest study looks at global efforts to shut down DDoS-for-hire ops. It shows a mix of achievements and frustrations as the underground market adapts and resurfaces. Full story here.
💌 Get this newsletter straight to your inbox
Sign up to our monthly Network Engineering Community News here