FastNetMon Advanced offers complete production-ready integration with a cloud DDoS scrubbing service called Magic Transit, provided by Cloudflare Inc. Cloudflare and Magic Transit are registered trademarks of Cloudflare Inc.
Please check that your version of FastNetMon is 2.0.357 or newer.
To use this capability, you will need to create an API key which allows you to control Magic Transit. You can do it from this page (click in the top right corner on "user" logotype, then select "My Profile". After that, on the left side select "API Tokens").
You need to create an API token that allows access only for Magic Transit and does not provide full control over the account.
Click "Create token", then on the page bottom select "Create Custom Token" and click "Get started".
- Token name: "fastnetmon"
- Permissions: "Account", "Magic transit", "Edit"
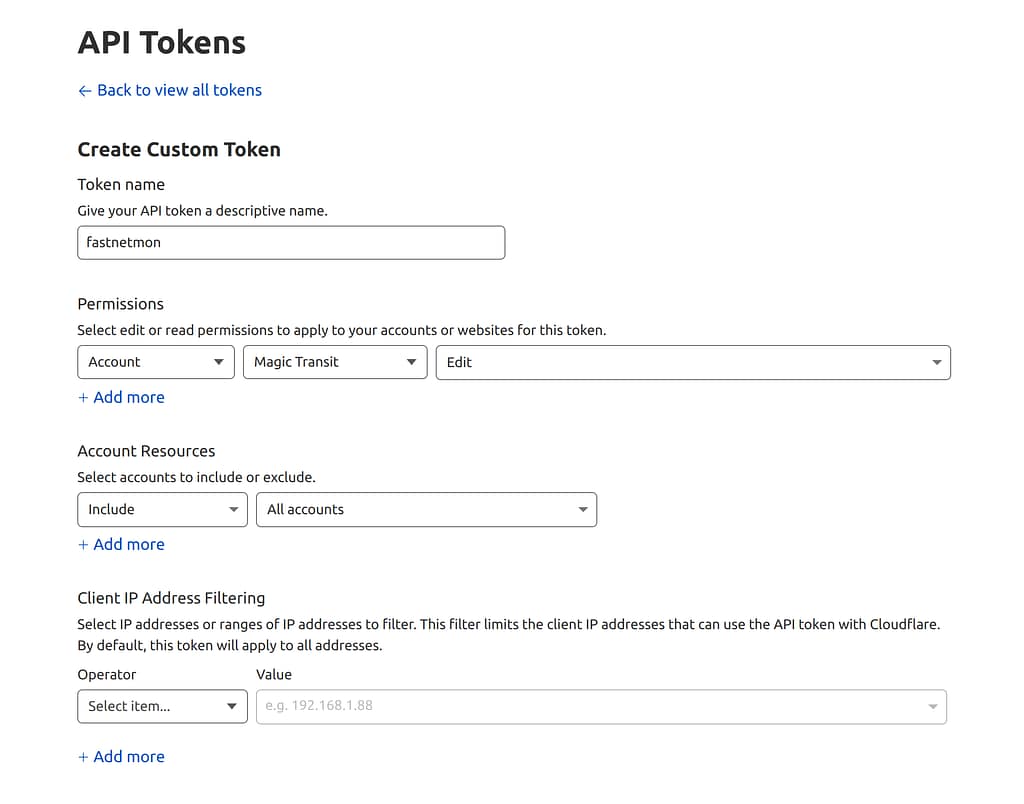
Then continue to Summary and then "Create token".
You will see a token in the format of a long, alphanumeric string; copy it.
In addition to the authentication token, you will need the account ID. To get it, you need to pick any domain, and then in the right panel you will see ZoneID and AccountID. If you do not have any domains at Cloudflare, then you need to open the main dashboard and, on the left menu, select "Manage account", "Members". Then you need to check the URL in your browser: "https://dash.cloudflare.com/xxxx/members". The long xxxx sequence is your AccountID.
How does FastNetMon scrubbing diversion automation work?
When FastNetMon detects an attack against an IP address, it determines /24 prefix for the IP which is under attack and then announces it to the scrubbing centre. When the attack stops or the ban time expires, FastNetMon removes the announce from the scrubbing centre using their API.
You can set a priority and weight as you wish; the next hop needs to be set to the value provided by the scrubbing centre.
Then use fcli to apply the configuration instead of editing the file manually:
sudo fcli set plugin scrubbing_services_integration provider_name cloudflare sudo fcli set plugin scrubbing_services_integration cloudflare_api_token yyy sudo fcli set plugin scrubbing_services_integration cloudflare_account_id xxx sudo fcli set plugin scrubbing_services_integration cloudflare_next_hop 10.20.30.40 sudo fcli set plugin scrubbing_services_integration cloudflare_priority 100 sudo fcli set plugin scrubbing_services_integration cloudflare_weight 100 sudo fcli set plugin scrubbing_services_integration log_path /var/log/fastnetmon/fastnetmon_scrubbing_services_integration.log
Finally, configure it on the FastNetMon side to call it when FastNetMon blocks/unblocks IP:
sudo fcli set main notify_script_enabled enable sudo fcli set main notify_script_format json sudo fcli set main notify_script_path /opt/fastnetmon/libraries/scrubbing_services_integration_plugin/scrubbing_services_integration sudo fcli commit
After that, we recommend manually blocking some IP addresses from the test prefix and checking that it works as expected.
You can do it this way:
sudo fcli set blackhole 1.2.3.4
And then to unblock the list of all blocked hosts with their UUIDs:
sudo fcli show blackhole
And unblock it:
sudo fcli delete blackhole <uuid>
Integration logic has very detailed logging, and you can find the log file here: /var/log/fastnetmon/fastnetmon_scrubbing_services_integration.log

