
Orange Polska mitigated a sizable DDoS attack on Christmas Eve, peaking at 1.5 Tbps. Orange Polska is the Polish national telecommunications operator and part of the Orange Group. The incident was first reported by the operator’s CERT team.
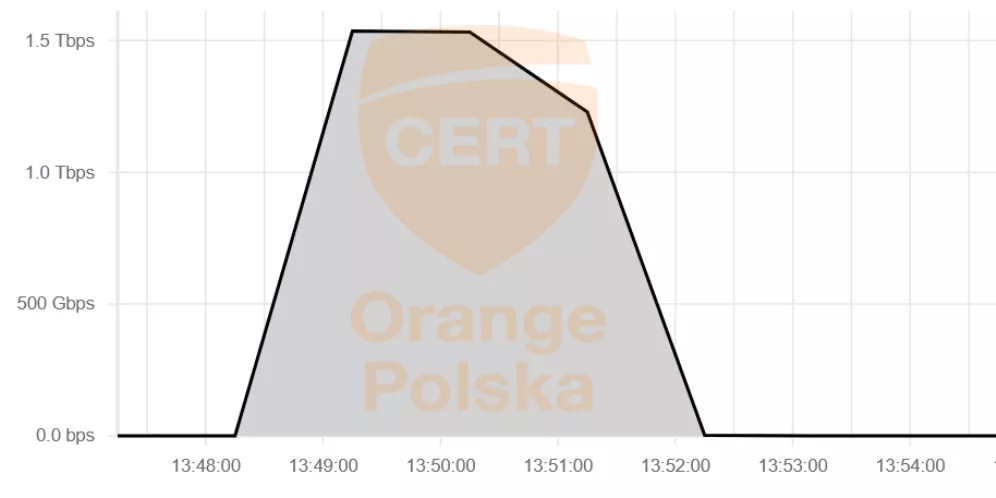
The timing of the attack is notable. Christmas Eve typically coincides with elevated baseline traffic levels and reduced operational staffing, conditions that can lower defensive margins and increase the likelihood of service impact. Despite this, Orange reported no customer-visible disruption.
Single-IP target, multi-vector execution
Unlike many large-scale attacks aimed at shared infrastructure, this campaign targeted a single IP address. This suggests the attacker’s objective was likely to overwhelm a specific service or user rather than cause widespread network instability. The case is part of a growing trend: terabit-scale DDoS attacks are no longer reserved for large public platforms and can now be directed at individual endpoints.
From a technical perspective, the attack was classified as a hyper-volumetric, multi-vector DDoS. Orange Polska identified the simultaneous use of:
- IP fragmentation floods
- DNS floods
- UDP floods
- NetBIOS amplification
- Total traffic floods
At peak, packet rates reached 134.5 million packets per second (Mpps), placing significant stress on both bandwidth and packet-processing capacity.
Largest for Orange, but far from global records
While 1.5 Tbps represents a record-breaking event within Orange Polska’s network, it remains well below the largest DDoS attacks reported globally in recent months. For comparison, Cloudflare disclosed a 29.7 Tbps DDoS attack linked to the Aisuru botnet in December 2025.
This contrast is becoming a familiar reality for many network operators: attack capacity continues to grow faster than most networks’ organic traffic growth, and even “mid-range” terabit attacks are now becoming operationally routine.
Effective mitigation, limited visibility
Orange confirmed that mitigation systems operated as designed, absorbing the attack without measurable impact on end users. However, the operator also cautioned against complacency. By nature, DDoS attacks leave little to no forensic trace on targeted systems, and successful mitigation can mask the true scale and frequency of these events.
For network engineers and security teams, the incident reinforces several lessons:
- Terabit-scale DDoS attacks are increasingly common at the national ISP level
- Single-IP targets can now attract extreme attack volumes
- Multi-vector floods remain the dominant tactic
- Continuous traffic visibility and fast, automated mitigation are critical
As attacker capabilities continue to scale, incidents like this demonstrate why real-time network traffic analysis and rapid mitigation remain foundational controls for modern ISP and enterprise networks.
About FastNetMon
FastNetMon is a leading solution for network security, offering advanced DDoS detection and mitigation. With real-time analytics and rapid response capabilities, FastNetMon helps organisations protect their infrastructure from evolving cyber threats.For more information, visit https://fastnetmon.com.