How compromised CUPS servers can be a DDoS threat?
A newly discovered vulnerability (CVE-2024-47850) in the Common Unix Printing System (CUPS) can be exploited to stage DDoS attacks. Starting an attack is surprisingly simple. It only requires sending a single packet to a vulnerable CUPS service, triggering an amplified, partially attacker-controlled IPP/HTTP request flood.
There are over 198,000 vulnerable CUPS devices accessible online, and roughly a third of them can be potentially used for abuse. Read on to get the full picture!
What is CUPS?
CUPS, or Common UNIX Printing System, is a modular printing system utilized by Unix-like computer operating systems. Simply put, CUPS allows a computer to act as a printer server, in a way that the computer running CUPS is a host, accepting print jobs from client computers, process them, and then send them to printers.
On September 26th 2024, security researcher Simone Margaritelli (also known as EvilSocket) discovered a vulnerability in CUPS that could potentially be exploited to stage DDoS attacks. This vulnerability is present in the "cups-browsed" package bundled with "cups-filters" and is triggered when a request to add a printer via UDP is received.
How does the vulnerability work?
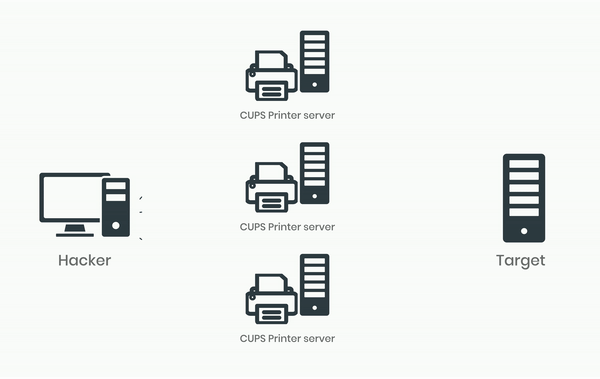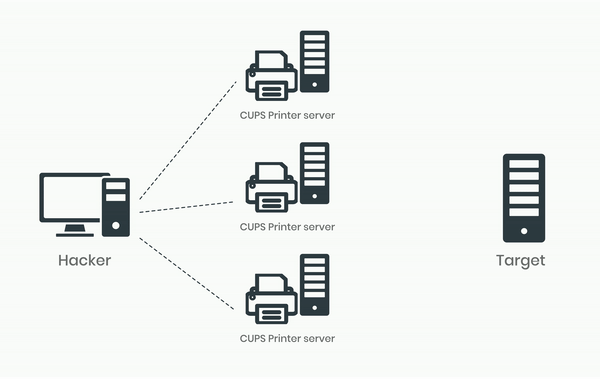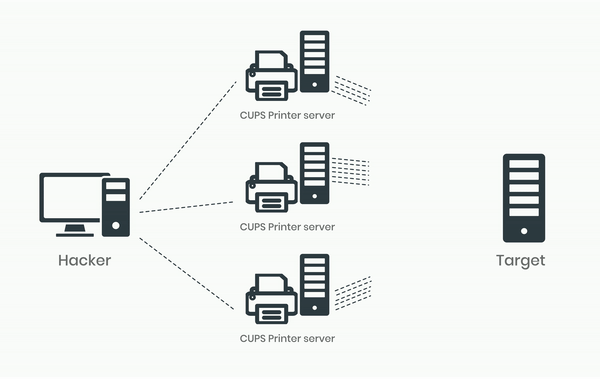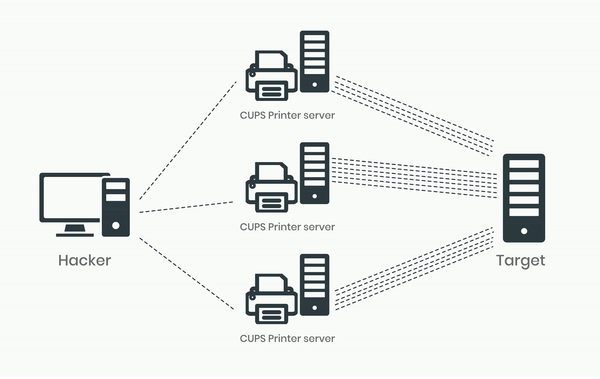
This vulnerability can be exploited for DDoS attacks by sending a single packet to a vulnerable and exposed CUPS service that is connected to the Internet. The attack prompts the CUPS service to generate a larger and partially attacker-controlled IPP/HTTP requests directed at a specified target. This not only affects the target but also the host of the CUPS server, as the attack consumes its network bandwidth and CPU resources.
How impactful is the CUPS vulnerability?
The impact and exposure of this CUPS vulnerability are significant, and we recommend immediate action. Some researchers have estimated that more than 198,000 devices are vulnerable and accessible on the public internet, and approximately 34% of these devices are potentially usable for DDoS abuse. Some of these vulnerable CUPS servers can establish thousands of requests, which indicates a serious potential for amplification.
Patching the vulnerability
Preventing the CUPS DDoS attacks involves either updating to the latest version of CUPS or removing it entirely, depending on your system's needs. If removal or updating isn't possible, we recommend firewalling the service ports, especially if they're accessible from the broader internet. Additionally, defenders should be prepared to identify and fend off attackers by implementing matching rules in their WAF configurations.
About FastNetMon
FastNetMon delivers versatile DDoS detection software for companies at any scale. With extensive experience in the telecom, mobile, and cloud computing industries, we take pride in preventing DDoS attacks and protecting our customers’ networks to the highest standard.
Find out more: https://fastnetmon.com/