APRICOT 2026 in Jakarta brought together one of the most technically sharp and operationally focused Internet communities we’ve seen this year. As Asia Pacific’s largest Internet operations...
Blog
NANOG 96 – Event Recap
FastNetMon attended NANOG 96, held 2–4 February 2026 in San Francisco, joining over 800 network engineers, operators, and architects for three days of technical talks, hallway debates, and community...
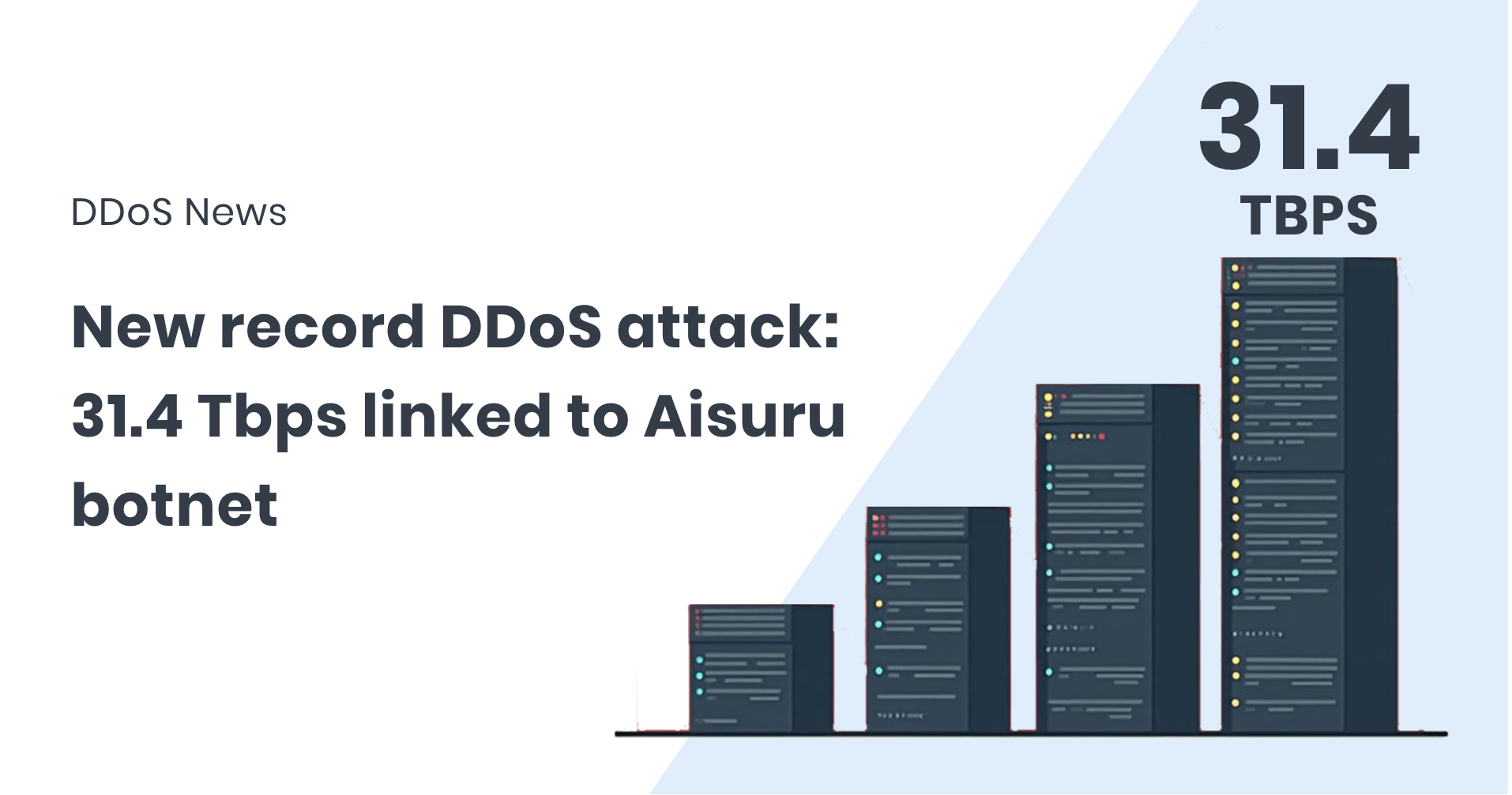
Aisuru botnet sets a new DDoS record at 31.4 Tbps
Another DDoS record has been reported, and once again, it is the same botnet setting it. In late January 2026, Cloudflare disclosed details of what is now the largest publicly reported DDoS attack...
Engineering deep dive: How AMS-IX uses FastNetMon for automated DDoS mitigation
Introduction DDoS attacks have long been a thorn in the side of network operators—but AMS-IX faced a particularly unusual challenge. Unlike the massive volumetric attacks that make headlines, the...
End may be near for Aisuru and Kimwolf botnets after large-scale C2 disruption
One of the largest DDoS botnet operations observed in recent years may be facing sustained disruption after hundreds of command-and-control (C2) servers linked to the Aisuru and Kimwolf botnets were...
OCCRP reports sustained DDoS attack targeting its investigative journalism website
The Organized Crime and Corruption Reporting Project (OCCRP) has reported that its website has been targeted by a large-scale DDoS attack, slowing access and making it difficult for readers to reach...
Venezuela’s routing anomaly and the bigger problem with BGP security
In early January 2026, unusual Internet routing behaviour was observed involving AS8048, operated by CANTV, Venezuela’s state-owned telecommunications provider. The anomalies were highlighted by...
DDoS attacks disrupt Final Fantasy XIV Savage raid launch
The launch of Final Fantasy XIV’s latest Savage raid tier in patch 7.4 was disrupted by a sustained wave of DDoS attacks, primarily affecting North American gamers. While European and Japanese...
BGP Blackhole Automation for DDoS mitigation
In this article, we will discuss how the routing infrastructure, more specifically the BGP routing technique called “blackholing”, can provide efficient mitigation for DDoS attacks. We will go...
Orange Polska mitigated a large multi-vector DDoS attack on Christmas Eve
Orange Polska mitigated a sizable DDoS attack on Christmas Eve, peaking at 1.5 Tbps. Orange Polska is the Polish national telecommunications operator and part of the Orange Group. The incident was...