- Network Layer DDoS Detection and Mitigation
Comprehensive Solution For DDoS Security
PRODUCT OVERVIEW
The Control Plane of Your DDoS Defence Stack
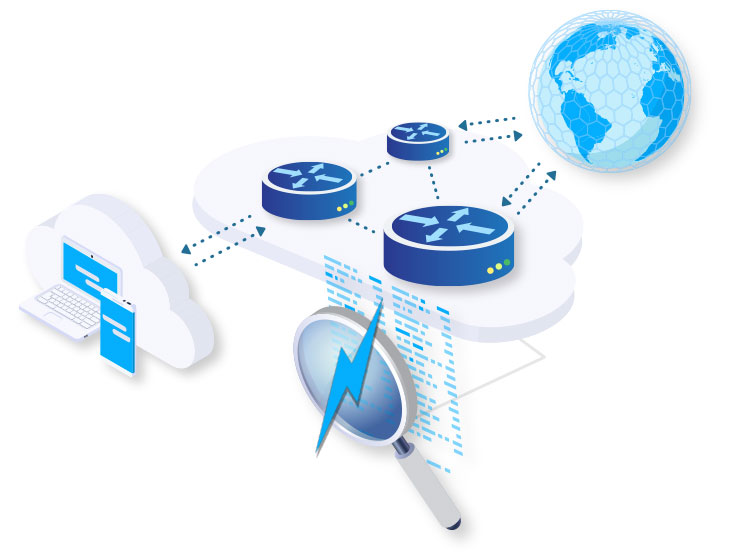
FastNetMon analyses live network traffic to detect DDoS attacks in near real time and triggers mitigation actions based on operator-defined rules and workflows. Engineers can use FastNetMon to initiate responses via BGP FlowSpec, RTBH, or redirect traffic to external scrubbing centres, while retaining full control over how, when, and where mitigation is applied within their network.
Partnered With the Very Best in the Ecosystem
Countries Worldwide
Deployments
Tbits
Peak performance
DDoS Detection
Real-time network traffic visibility
FastNetMon continuously analyses live traffic to detect DDoS attacks in near real time while providing visibility into traffic volumes, packet rates, and protocol behaviour. Detection thresholds and mitigation workflows are defined upfront, enabling automated response when attack conditions are met.
RTBH Automation
Automated BGP blackholing for rapid attack containment
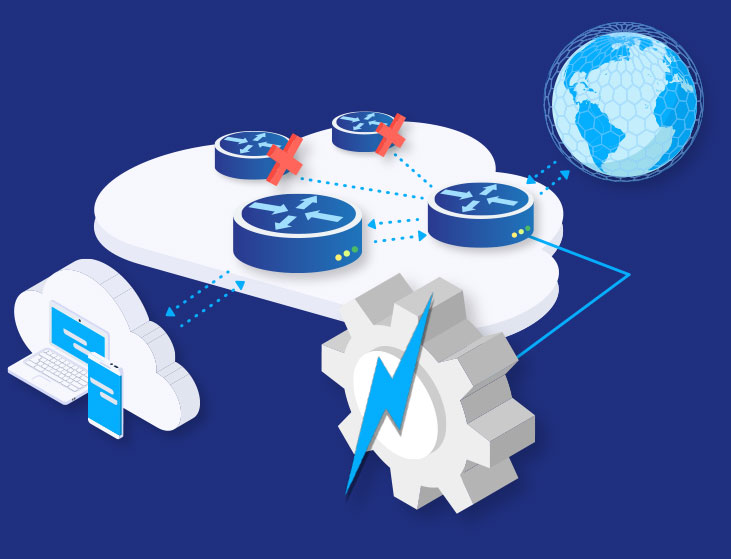
FastNetMon automates remote-triggered blackholing (RTBH) for high-volume DDoS scenarios where temporarily dropping all traffic to a targeted IP or prefix is preferable to risking congestion or instability across the rest of the network. Operator-defined policies control when blackholing is applied and automatically withdrawn once conditions return to normal.
BGP Flow Spec
Targeted traffic filtering using BGP Flow Spec rules
FastNetMon manages Flow Spec rules based on operator-defined thresholds and policies. When traffic crosses configured thresholds, it automatically creates and announces BGP Flow Spec rules to filter or rate-limit specific attack patterns. Configurable unban logic ensures rules are withdrawn after conditions normalise, so filtering is applied only when needed.


Scrubbing Centre Diversion
Automated traffic diversion to external mitigation systems
FastNetMon detects attacks and automatically diverts affected traffic to scrubbing centres using routing-based controls. Engineers define when diversion occurs and which prefixes are redirected, enabling seamless integration with on-premises or third-party scrubbing infrastructure.
OUR CUSTOMERS
Protecting Some of the World’s Largest Networks
FastNetMon is deployed by telecommunications providers, ISPs, hosting companies, and enterprises operating networks of all sizes. From regional operators to global infrastructure providers, customers rely on FastNetMon to protect production networks from DDoS attacks while maintaining control over their routing and mitigation workflows.
Modern DDoS defence, without legacy pricing
FastNetMon delivers network-level DDoS detection and mitigation without the cost or complexity of traditional solutions. Entry plans start at $115/month, scaling to meet enterprise and ISP requirements.
Latest News
NANOG 96 – Event Recap
FastNetMon attended NANOG 96 , held 2–4 February 2026 in San Francisco, joining over 800 network engineers, operators, and architects for three days of technical talks, hallway debates, and…
Aisuru botnet sets a new DDoS record at 31.4 Tbps
Another DDoS record has been reported, and once again, it is the same botnet setting it. In late January 2026, Cloudflare disclosed details of what is now the largest publicly reported DDoS attack…
Venezuela’s routing anomaly and the bigger problem with BGP security
In early January 2026, unusual Internet routing behaviour was observed involving AS8048, operated by CANTV, Venezuela’s state-owned telecommunications provider. The anomalies were highlighted by…
BGP Blackhole Automation for DDoS mitigation
In this article, we will discuss how the routing infrastructure, more specifically the BGP routing technique called “blackholing”, can provide efficient mitigation for DDoS attacks. We will go…







































