In this document, we will help you to set up FastNetMon in sFlow, Netflow / IPFIX or mirror mode. To start this process, you should have installed FastNetMon.
Common steps
You need to finish these steps for all available capture methods (sFlow, NetFlow, IPFIX, Mirror).
Please enumerate all your IPv4 and IPv6 networks in CIDR form:
sudo fcli set main networks_list 11.22.33.0/22 sudo fcli set main networks_list beef::1/64 sudo fcli commit
We need this information to properly detect the traffic direction. Please note that you cannot use wildcard prefixes like 0.0.0.0/0 as FastNetMon explicitly ignores them in networks_list.
If you have a large number of networks and they change frequently, we have options to read the network list directly from BGP peering connection. Please refer to this guide.
Enable traffic capture
FastNetMon supports a variety of traffic telemetry protocols. Usually, routers support Netflow or IPFIX. Switches do support sFlow. In case if none of these protocols are supported, you may rely on port mirror.
- Netflow v5, v9, v10 (IPFIX)
- sFlow
- Port mirror
- Nokia L3 sampled mirror
- FastNetMon Flow
- Amazon AWS VPC Flow logs
- Google GCE VPC Flow logs
How to check if it is working?
The best way to confirm that FastNetMon calculates traffic correctly is to run command-line client:
fastnetmon_client
It will show a window like this:
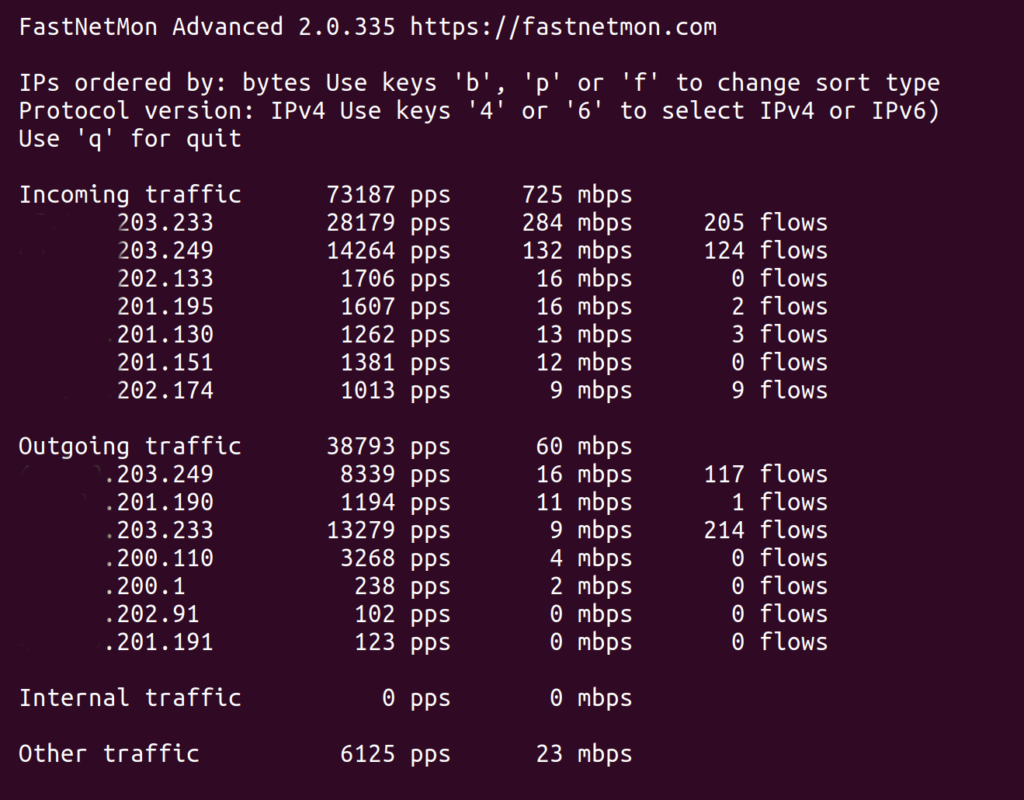
Alternatively, you can use the command-line tool fcli to see total traffic for IPv4 and IPv6 protocols:
sudo fcli show total_traffic_counters sudo fcli show total_traffic_counters_v6
If telemetry was set up correctly, you should see non-zero counters for incoming and outgoing traffic.
Total traffic counter types:
- Other traffic - “nor source nor destination is known to be part of our list of networks”. Also, it may be a non-IP (for example, ARP) traffic too
- Internal traffic - traffic where source and destination both belong to your list of networks. FastNetMon does not trigger DDoS alerts for such traffic at all
If you see a significant amount of other traffic, then it may bea good idea to enable the following option temporarily to dump all flows classified as other to /var/log/fastnetmon/fastnetmon.log to find all networks you've missed during setup:
sudo fcli set main dump_other_traffic true sudo fcli commit
You could check the load for all your IPv4 and IPv6 networks in the following way:
sudo fcli show network_counters sudo fcli show network_counters_v6
To see the top 10 IPv4 or IPv6 hosts in your network, you can use the following command:
sudo fcli show host_counters bytes outgoing sudo fcli show host_counters_v6 bytes outgoing
To get traffic for specific IPv4 or IPv6 hosts, you can use the following command:
sudo fcli show single_host_counters 10.1.2.3 sudo fcli show single_host_counters_v6 beef::1
Detection modes
FastNetMon offers multiple ways to defend your network from DDoS attacks:
- Blackhole mode, in this mode FastNetMon blocks the attacked host using BGP Blackhole and effectively unplugs it from the Internet to move malicious traffic away from your network and keep its uptime.
- Total hostgroup logic offers the ability to create BGP announces or alerts when the total traffic for a group of networks exceeds a defined value. It may be useful as defence against carpet bombing attacks and as a reliable trigger for traffic diversion to DDoS scrubbing centres.
- BGP Flow spec based mitigation, in this mode, FastNetMon can isolate only malicious traffic and filter it out using your routers.
- Remote host blocking offers an option to block attackers using the BGP protocol.

