FastNetMon Blog: DDoS News & Network Security Insights
FastNetMon Blog brings you the latest DDoS news, expert analysis, and technical insights on DDoS attacks and network security. As the leading source for DDoS-related content, we cover new threats, attack trends, and protection strategies. Our articles are written for network engineers, security teams, and tech professionals who want to stay ahead of evolving cyber threats. Follow us for updates, how-to guides, and research from the front lines of DDoS defence.
One of the largest DDoS botnet operations observed in recent years may be facing sustained disruption after hundreds of command-and-control (C2) servers linked to the Aisuru and Kimwolf botnets were t…
The Organized Crime and Corruption Reporting Project (OCCRP) has reported that its website has been targeted by a large-scale DDoS attack, slowing access and making it difficult for readers to reach i…
In early January 2026, unusual Internet routing behaviour was observed involving AS8048, operated by CANTV, Venezuela’s state-owned telecommunications provider. The anomalies were highlighted by Gra…
The launch of Final Fantasy XIV’s latest Savage raid tier in patch 7.4 was disrupted by a sustained wave of DDoS attacks, primarily affecting North American gamers. While European and Japanese regio…
Orange Polska mitigated a sizable DDoS attack on Christmas Eve, peaking at 1.5 Tbps. Orange Polska is the Polish national telecommunications operator and part of the Orange Group. The incident was fir…
A new “super botnet” Kimwolf reported by researchers Security researchers at XLab reently disclosed Kimwolf, a newly identified Android-based botnet that has allegedly infected more than 1.8 milli…
DDoS News: France’s national postal service, La Poste, has confirmed that a DDoS attack disrupted its digital infrastructure, partially taking services offline and slowing parcel deliveries just bef…
On December 16, 2025, Solana reported that its network had been under a sustained DDoS attack for approximately a week, with traffic peaking near 6 Tbps. Solana described the event as the fourth-large…
CISA, together with the FBI, the Department of Energy, the EPA, and international partners, have issued a joint advisory highlighting ongoing DDoS and intrusion attacks targeting operational technolog…
This article is written by Herve Hildenbrand and was originally published on LinkedIn. Reposted with the author’s permission. A DDoS attack almost ruined my 40th birthday. Not the party, but the inf…
One of the most common ways to protect a network from large volumetric DDoS attacks is to divert the malicious traffic to a scrubbing centre. These dedicated networks remove harmful packets and return…
DDoS news: December 4th 2025 A new world-record DDoS attack has been confirmed, peaking at 29.7 terabits per second (Tbps) and launched by the Aisuru botnet, a large DDoS-for-hire network using an est…
Every time law enforcement announces a major DDoS botnet operation, the Internet seems to exhale in relief. Servers are seized, operators arrested, domains pulled out from under them. For a moment, at…
During late October 2025, a new Mirai-derived botnet dubbed ShadowV2 was observed exploiting unpatched IoT devices across multiple sectors and 28 countries. While the activity lasted only a day, it un…
This week, Microsoft confirmed it had mitigated the largest DDoS attacks ever observed on Azure: a 15.72 Tbps, 3.64 Bpps barrage against a single public IP endpoint in Australia. The attack was powere…
The U.S. Department of the Treasury, together with the UK and Australia, has announced coordinated sanctions against a network of Russian “bulletproof” hosting providers (BPH) used to run ransomwa…
Researchers are tracking a self-replicating botnet campaign, ShadowRay 2.0, that is targeting internet-facing Ray clusters, the open-source distributed computing framework used to run AI and other wor…
The European Union’s cybersecurity agency, ENISA, has published a new sectorial threat landscape report and a press release showing that public administrations are increasingly targeted by cyber-att…
In early November 2025, Belgian networks were hit by two related DDoS campaigns targeting telecom operators, healthcare services, and military-intelligence websites. The pro-Russian hacktivist group N…
We are pleased to welcome a guest contributor: BGP Brian (Brian Wilson). Brian leads the BGP Black Belt training community and the consultancy BGP Engineering and Design Group, and is an active voice …
The Aisuru botnet, responsible for multiple record-breaking DDoS attacks this year, has reportedly altered its operations to supply infected IoT devices for use as residential proxies. This marks a sh…
Poland’s largest digital payment service, BLIK, has suffered periodic outages after being targeted by distributed denial-of-service attacks over the weekend and into Monday. The incidents caused int…
A newly emerged hacktivist collective calling itself Hezi Rash (‘Black Force’) has sharply increased DDoS activity across multiple countries. Between August and October 2025, researchers observed …
Russia’s national food-safety regulator, Rosselkhoznadzor, faced a DDoS incident last week that took down its digital certification systems and disrupted product shipments across the country. What h…
Every now and then, a network operator’s inbox lights up with a DDoS ransom note — bold claims, big threats, and a bitcoin address waiting for payment. We’ve seen plenty of them ourselves. Some …
Aisuru, a massive IoT botnet, recently pushed outbound traffic close to 30 Tbps from infected devices inside major U.S. ISPs — one of the largest DDoS events ever recorded. Outbound DDoS attacks, wh…
Today, FastNetMon protects networks of all sizes from DDoS attacks and serves customers in dozens of countries worldwide. But how did it all begin? This is the story of the company’s early days�…
Recent kernel updates led by Google engineer Eric Dumazet, and first reported by Michael Larabel (Phoronix), show that Linux 6.18 delivers significant improvements in how servers handle high-rate DDoS…
Guest post by Vincentas Grinius, Co-Founder at IPXO The shift to IPv6 has escalated into a matter of national security, as nations lagging in adoption are increasingly exposed to cyber threats and dim…
Incident summary: What we know so far Several major gaming platforms — including Steam and Riot Games — experienced simultaneous disruptions on October 6th. Players reported widespread connectivit…
ShadowV2 has been identified as a new DDoS-as-a-service platform that stands out for its use of cloud infrastructure. Instead of relying on home routers or compromised IoT devices, it exploits misconf…
When we talk about DDoS attacks, the focus is almost always on protecting services from inbound floods. But there’s another side to the story that often goes unnoticed: outbound DDoS attacks. These …
The cybersecurity landscape witnessed a new benchmark in DDoS attacks as Cloudflare reported mitigating a hyper-volumetric assault that peaked at 22.2 terabits per second (Tbps) and 10.6 billion packe…
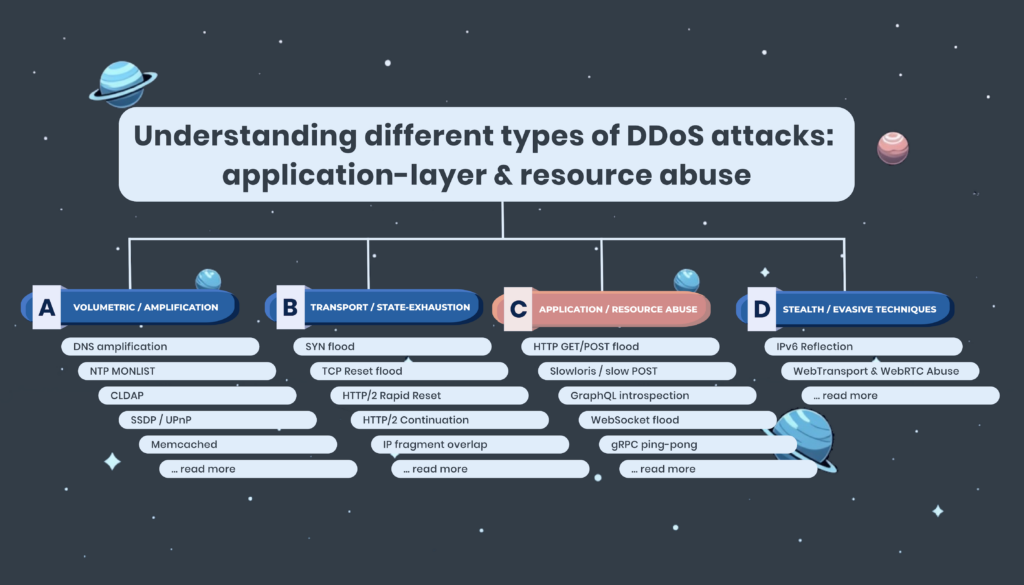
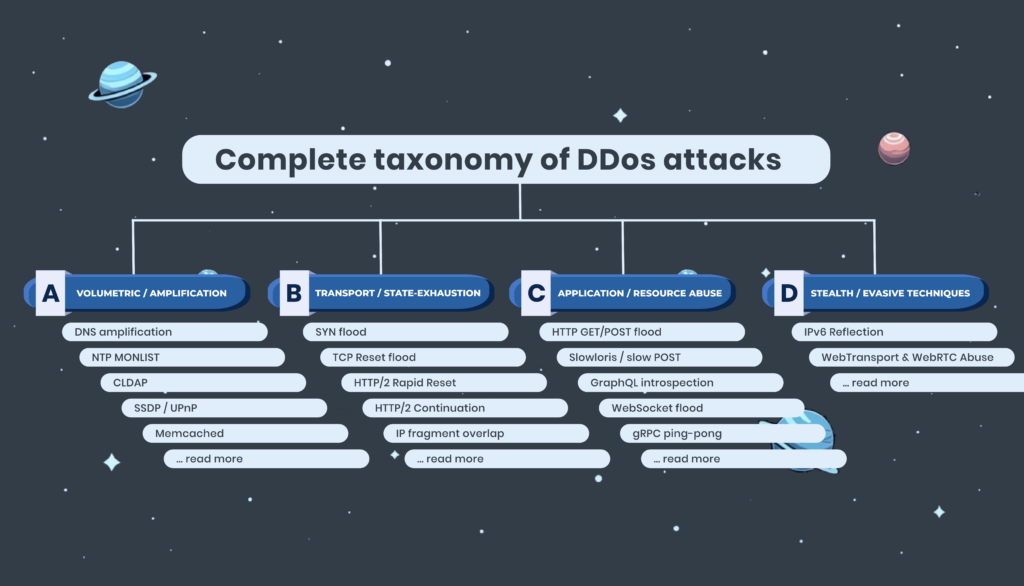
What L3 and L4 DDoS attacks are, how they work, and what defenders need to know DDoS attacks at Layers 3 and 4 (the Network and Transport layers) are some of the most common and disruptive seen on the…
DDoS attacks remain one of the most disruptive threats facing ISPs, backbone networks, hosting providers, and enterprises. Detecting the attacks quickly is essential to keeping networks stable and ser…
Researchers from the University of Cambridge’s Security Group recently published important findings on the effectiveness of global law enforcement actions against DDoS-for-hire services, also known …
Despite being a decades-old threat, DDoS attacks still come with a cloud of misunderstanding. Every time a myth goes unchecked, organisations risk underestimating threats or misallocating resources. T…
Breaking DDoS news from FastNetMon At FastNetMon, we recently worked with a customer — a DDoS scrubbing provider — who faced one of the largest DDoS attacks ever publicly recorded. This disclosure…
Application-layer and “low-and-slow” DDoS attacks explained by DDoS defence professionals Application-layer (L7) and “low-and-slow” DDoS attacks are among the most insidious forms of denial-of…
Introduction: Questions you always wanted to ask about DDoS DDoS is one of those topics that everyone in the industry has heard about, but few feel confident they fully understand. Maybe you’ve sat …
Cloudflare has disclosed that it successfully mitigated the largest DDoS attack recorded to date — a hyper-volumetric UDP flood peaking at 11.5 terabits per second (Tbps). The attack lasted only 35 …
We often talk about how DDoS attacks happen — via botnets, traffic floods, vectors — but rarely do we ask the more human question: why? The truth is, behind every DDoS attack is a motive. Sometime…
The Arch Linux project has confirmed that its core infrastructure has been under sustained DDoS attack for more than a week. The campaign, which began on August 16, 2025, has disrupted user access to …
DDoS defence explained: how to detect and mitigate a DDoS attack? DDoS attacks are easier than ever to launch, harder to trace, and can cause real damage if you’re not prepared. The end result i…
The U.S. Department of Justice has charged a 22-year-old Oregon man for operating RapperBot, a large-scale botnet-for-hire that powered more than 370,000 DDoS attacks between April and August 2025. Bu…
MadeYouReset is a new HTTP/2 DDoS vector related to 2023’s Rapid Reset. By provoking the server to reset streams with malformed frames, an attacker keeps backend request processing alive while…
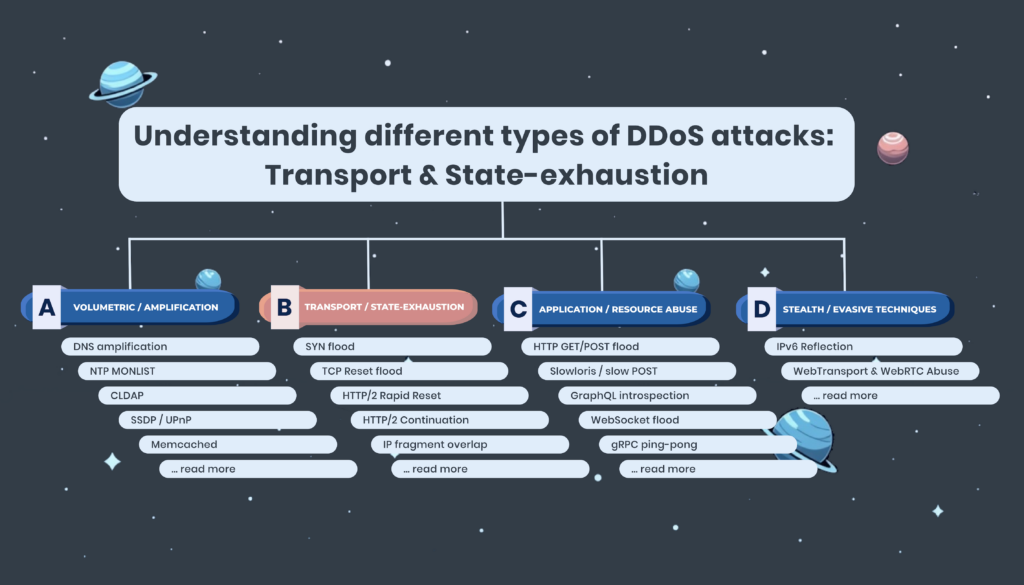
How connection state exhaustion attacks threaten your firewalls and proxies Transport and state-exhaustion DDoS attacks represent a growing and sophisticated category of denial-of-service threats targ…
SafeBreach Labs researchers Or Yair and Shahak Morag disclosed a new class of Windows denial-of-service (DoS) vulnerabilities that can be exploited to crash critical infrastructure or conscript public…
As DDoS attacks grow in scale and complexity, modern mitigation strategies are evolving to meet the challenge. Organisations today have more powerful tools than ever—but success hinges on speed, aut…
If you’ve managed a network for more than a week, chances are you’ve seen it, or at least worried about it: the DDoS attack. You know the symptoms. Traffic spikes. Routing instability. Customers r…
August 3, 2025, a crypto mining pool called Qubic claimed it was hit by a Distributed Denial-of-Service (DDoS) attack after launching an aggressive bid to gain control of the Monero blockchain. While …
In 2025, network traffic visibility isn’t just a technical requirement—it’s a strategic necessity. As networks grow in size and complexity, visibility has become critical to performance, securit…
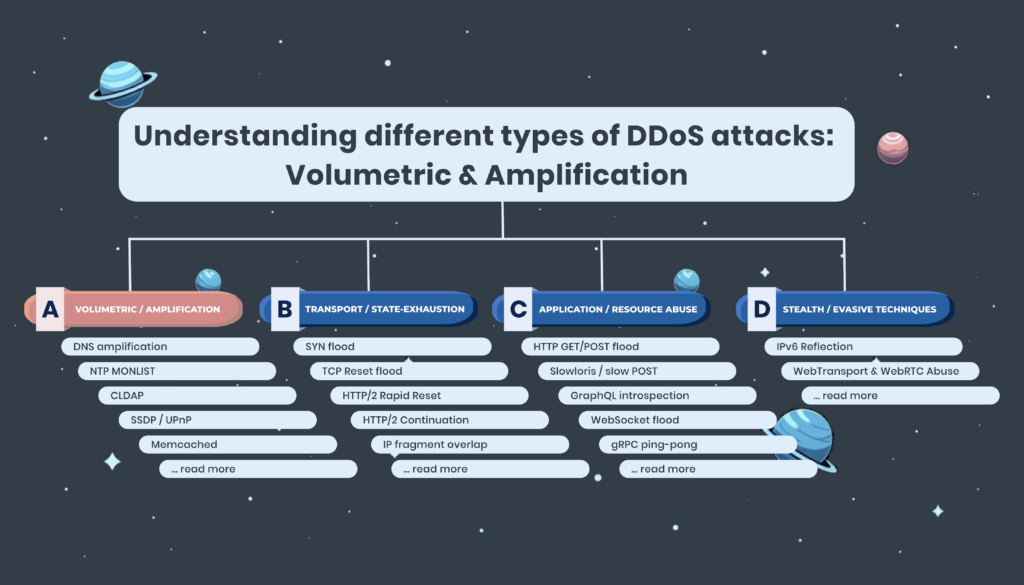
How bandwidth-focused DDoS campaigns work—and why they’re still effective at scale Volumetric DDoS attacks remain one of the most common and disruptive forms of denial-of-service activity across t…
AhnLab Security Intelligence Center (ASEC) has recently uncovered a wave of malicious activity involving the SVF Botnet, a lightweight yet capable Python-based malware used to launch DDoS attacks via …
A practical breakdown of DDoS attack vectors, built for network operators When your NOC wallboard lights up red, you don’t have 5 seconds. And if you’re relying on manual triage at that point, it …
On July 21, 2025, the Hungarian National Investigation Bureau’s Cybercrime Investigation Unit announced the arrest of a 23-year-old suspect behind a series of coordinated DDoS attacks targeting the …
In a major win for cybersecurity defenders across Europe, Europol and Eurojust have successfully coordinated an international operation—Operation Eastwood—to disrupt the infrastructure and operati…
The Modern Era: from modular loaders to multi-vector flood engines As defenders have become more aware of the classic tactics used by earlier botnets like BASHLITE, Mirai, and GameOver Zeus, threat ac…
Juniper Networks has disclosed a new vulnerability (CVE-2025-52953) affecting Junos OS and Junos OS Evolved, which allows an unauthenticated adjacent attacker to send a valid BGP UPDATE packet that re…
Distributed Denial of Service (DDoS) attacks at layers 3 and 4 are blunt, fast, and disruptive. If you’re running networks at any scale, chances are you’ve already seen your fair share of UDP floo…
In a continuing wave of new malware activity, researchers have uncovered a botnet dubbed RondoDox, which is actively exploiting known vulnerabilities in TBK digital video recorders (DVRs) and Four-Fai…
A newly discovered botnet family dubbed Hpingbot is gaining attention in the cybersecurity community for its novel approach to malware delivery and DDoS execution. Detected by NSFOCUS’s Fuying Lab i…
For over two decades, botnets have been at the heart of some of the most disruptive activity online – from large-scale DDoS campaigns to credential theft and malware distribution. While the end …
Threshold-based DDoS defence is one of the most effective ways to automate blackhole routing for high-volume attacks, without the need for constant manual oversight. In this post, we’ll break down h…
Grinding Gear Games (GGG), the developer of the action RPG Path of Exile, has implemented new security updates to strengthen its protection against Distributed Denial‑of‑Service (DDoS) attacks. Th…
A new variant of the Flodrix botnet has entered the scene, and it’s taking aim at poorly secured open-source tools with an unusual level of stealth and versatility. The newest Flodrix variant builds…
Comprehensive resources on Distributed Denial of Service (DDoS) attacks are surprisingly hard to come by—especially ones that are both technically accurate and grounded in real-world experience. Tha…
The Internet Just Survived the Largest DDoS Attack Ever—Here’s What You Need to Know A new milestone in Distributed Denial of Service (DDoS) attacks has been reached: 7.3 terabits per second (Tbps…
Historically, DDoS attacks focused on obvious targets: banks, telecoms, gaming platforms, and government services. But in 2025, the landscape has shifted. Today’s DDoS campaigns are increasingly aim…
BGP Blackholing, also known as RTBH (Remotely Triggered Black Hole), is a well-established technique in the DDoS mitigation playbook. It’s fast, effective, and uses your upstream providers’ infras…
Botnets are behind some of the biggest online attacks we’ve seen in recent years. They don’t usually rely on advanced hacking techniques or zero-day exploits. Instead, they quietly take over poorl…
If your organisation buys bandwidth from one of the big backbone carriers, you already sit behind formidable pipes and global scrubbing clouds. Sales decks often call this ‘built-in DDoS protection�…
As of June 2025, the BYOND game engine continues to face a persistent and disruptive Distributed Denial-of-Service (DDoS) attack that began on May 10. This sustained assault has severely impacted BYON…
DDoS protection in cloud or on-premise: pros, cons, and the rise of hybrid defences Distributed-Denial-of-Service attacks used to be the headache of large carriers and gaming giants. Today they reach …
Effective DDoS Mitigation Strategies: Building a Tiered Defence System DDoS attacks still remain one of the most persistent and disruptive cyber threats in today’s internet infrastructure. From volu…
On 12 May 2025, digital-forensics journalist Brian Krebs watched his site absorb a flood of traffic that briefly touched 6.3 terabits per second. The surge lasted just 45 seconds, delivering about 585…
New Windows botnet HTTPBot zeroes in on game and tech portals For years, most DDoS botnets have operated from compromised routers, IoT devices, or Linux servers. HTTPBot breaks that pattern. Written i…
The rise of DDoS in global conflicts With societies increasingly dependent on online services, the front lines of geopolitical conflict are no longer limited to physical borders. Increasingly, state-s…
DDoS escalates alongside India-Pakistan hostilities When military tensions flared between India and Pakistan in early May, a parallel cyber campaign unfolded at speed. Threat-hunting data show a clear…
NoName057(16) ‘punishes’ the Dutch government by sending the largest single DDoS burst at their public services sector NoName057(16), the infamous hacktivist crew that has spent two years pepperin…
A successful international operation takes down several IP booter services In a major international crackdown on cybercrime, Polish authorities have arrested four individuals suspected of running a ne…
Some of the largest IP booter services listed – and what happens if you use them Hiring a DDoS attack used to mean building a botnet or knowing someone who had. Booter services changed all that:…
On 3 April 2025, an online bookmaker was battered by the largest public DDoS disclosed so far in 2025. As reported by Techradar, the traffic began spiking at 11:15 UTC, jumped from 67 Gbps to 217 Gbps…
Speculation of a cyber attack and data centre vulnerability raises concerns amidst a blackout in southern Europe In a dramatic turn of events, a widespread power outage has left millions across Spain,…
Dutch payment processor experiences multiple DDoS attacks in one day An evening of false starts Just after 7 p.m. on 8 April, diners in Dutch cafés and shoppers across Europe noticed card readers fre…
Evolution of DDoS: From single PCs to Terabit floods Twenty‑five years ago a teenager with a dial‑up modem discovered he could knock Yahoo! offline by hammering it with junk traffic. Since then de…
The notorious cybercrime marketplace BreachForums has gone offline once more, but this time, no one’s quite sure who’s behind it. While some suspect another FBI takedown, a group calling itself th…
What’s the difference between DoS, DDoS, RDoS, and how to prevent these cyberattacks? Not all cyberattacks are created equal. If you’ve ever heard terms like DoS, DDoS or RDoS and wondered what th…
Late March, a well-known Dutch web hosting provider, Argeweb, found itself under fire from a DDoS attack that spiralled into a week-long struggle to stay online. What started as a few complaints about…
“DDoS for hire” – how anyone can pay to take down a website You don’t need to be a hacker to launch a cyberattack anymore. These days anyone with £20 and a few minutes can rent a …
On 1 April, Russia’s state-owned railway RZD was hit by a DDoS attack that knocked its website and mobile app offline. No tickets, no timetables, just timeout errors The disruption began Tuesd…
What can we learn from the alleged high-profile cyber attack? Earlier this month, social media platform X (formerly Twitter) experienced a major DDoS attack that caused intermittent outages for users …
Understanding DDoS Attacks from the hosting provider’s point of view As the backbone of the internet, hosting providers are pivotal in defending against DDoS attacks. Their ability to maintain the a…
One of World of Warcraft Hardcore’s most watched guilds, OnlyFangs, has officially disbanded — not because of in-game failure, but due to repeated DDoS attacks. The group, made up of streamers and…
A major DDoS attack hit South Africa’s CO.ZA domain services, leaving businesses and users unable to access websites linked to the country’s most widely used domain. The ZA Registry Consortium con…
Imagine trying to file your taxes or access your medical records, only to find the system completely down. That’s what happened with DigiD, the Dutch government’s login system. Twice. A large DDoS…
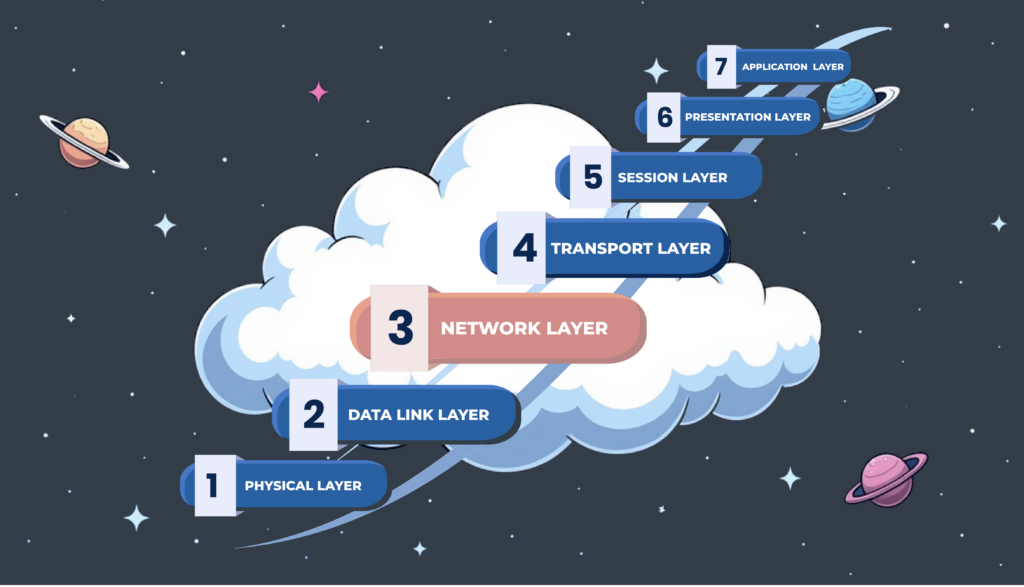
What are L3 DDoS attacks, and how do they work? Layer 3 DDoS attacks are a type of cyber assault that targets the third layer of the OSI (Open Systems Interconnection) model, which is responsible for …
Azerbaijan has faced a series of massive DDoS attacks targeting state information resources. The country’s digital infrastructure is challenged as the attacks have been disrupting the services and o…
A newly identified botnet, Eleven11bot, has emerged as a significant cyber threat, compromising over 80,000 internet-connected devices globally. Nokia Deepfield’s Emergency Response Team (ERT) has r…
What happened? E8 Markets, a well-known name in prop trading, faced a significant DDoS attack over the weekend, leaving traders locked out of their accounts for two days. Even as markets reopened on M…